Top API Security Best Practices to Protect Your Data
Discover essential API security best practices to safeguard your data. Learn how authentication, validation, and more can strengthen your API security.
Protecting Your APIs in the Modern Landscape
APIs drive modern applications, but also present security risks. This listicle provides eight essential API security best practices to safeguard your data and services. Learn how to implement critical security measures like OAuth 2.0, API gateways, TLS/SSL encryption, input validation, rate limiting, security headers, API monitoring, and JWTs. Applying these API security best practices is crucial for protecting your systems and building user trust.
1. OAuth 2.0 and OpenID Connect Authentication
Implementing robust security measures is crucial for protecting APIs from unauthorized access and data breaches. OAuth 2.0 and OpenID Connect (OIDC) are fundamental components of modern API security best practices. OAuth 2.0 is the industry-standard protocol for authorization, granting third-party applications limited access to user resources without requiring them to share their credentials. OpenID Connect builds upon OAuth 2.0, adding an identity layer that enables secure authentication and single sign-on (SSO) capabilities. Together, they provide a comprehensive framework for securing your APIs.
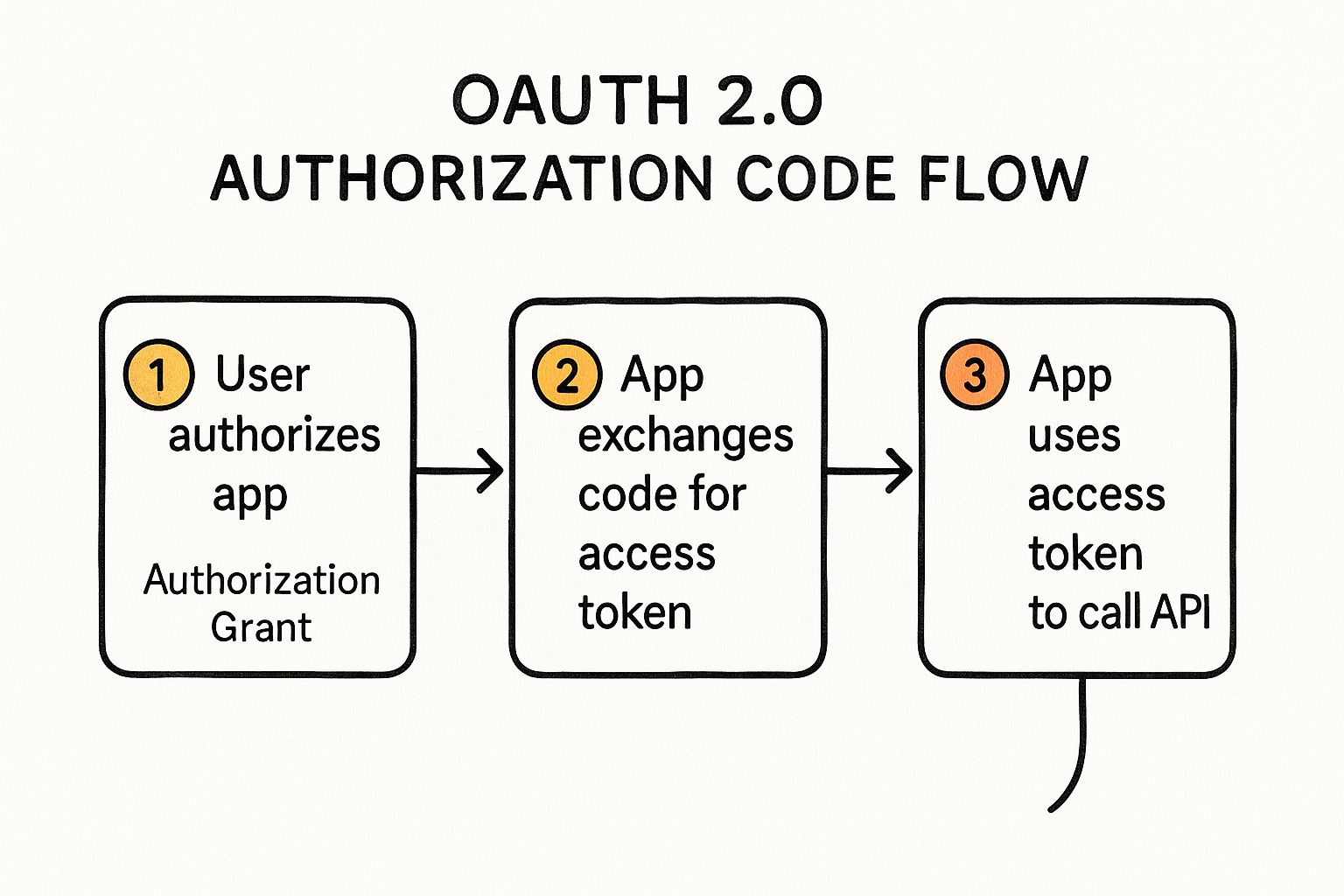
The infographic illustrates the typical OAuth 2.0 and OIDC flow. The process begins with the client application requesting authorization from the authorization server. The user then authenticates with the authorization server, granting permission to the client. Following this, the authorization server issues access and refresh tokens to the client. Finally, the client uses the access token to access the protected resource. This flow ensures that the client application never directly handles user credentials, significantly enhancing security.
This approach leverages token-based authorization, offering various authorization flows tailored to diverse use cases. This flexibility allows developers to choose the most suitable flow depending on the specific requirements of their application, contributing to enhanced API security best practices. Features such as scoped access permissions ensure that applications only receive access to the resources they explicitly need, further minimizing potential security risks. This granular control is essential for maintaining a robust security posture.
When and Why to Use OAuth 2.0 and OIDC:
You should consider OAuth 2.0 and OIDC whenever you need to grant third-party applications access to user data or resources without sharing sensitive credentials. This is particularly important in scenarios involving mobile apps, single-page applications (SPAs), and server-side applications interacting with APIs. This approach is crucial for enhancing API security best practices.
Pros:
- Eliminates the need for applications to handle user credentials.
- Provides fine-grained access control with scoped permissions.
- Widely adopted and well-documented, ensuring broad compatibility and ample resources.
- Facilitates centralized authentication, simplifying user management.
Cons:
- Can be complex to implement initially, especially for beginners.
- Requires careful management of tokens, including secure storage and revocation.
- Potential vulnerability to Cross-Site Request Forgery (CSRF) attacks if not implemented correctly.
- Demands rigorous security configuration to prevent vulnerabilities.
Examples of Successful Implementations:
- Google uses OAuth 2.0 for API access, allowing third-party applications to integrate with Google services.
- Microsoft Azure AD B2C leverages OpenID Connect for secure authentication and authorization.
- Auth0, a popular identity platform, utilizes OIDC to protect APIs and enable seamless single sign-on experiences.
Actionable Tips for Implementing OAuth 2.0 and OIDC:
- Always use HTTPS: Encrypt all communication between the client, authorization server, and resource server to prevent eavesdropping.
- Implement PKCE (Proof Key for Code Exchange): This is essential for protecting authorization codes in public clients, such as mobile apps.
- Use short-lived access tokens and longer-lived refresh tokens: This limits the potential damage of a compromised access token.
- Validate all tokens on the server-side: Never trust tokens without verification.
- Implement proper token revocation mechanisms: Ensure that compromised tokens can be quickly invalidated.
Learn more about OAuth 2.0 and OpenID Connect Authentication
OAuth 2.0 and OpenID Connect are foundational components of API security best practices. Their widespread adoption, robust features, and strong security capabilities make them indispensable tools for protecting your APIs and user data. By understanding and implementing these technologies effectively, you can significantly improve the security posture of your applications and safeguard against unauthorized access.
Get started with your lifetime license
Enjoy unlimited conversations with MultitaskAI and unlock the full potential of cutting-edge language models—all with a one-time lifetime license.
Demo
Free
Try the full MultitaskAI experience with all features unlocked. Perfect for testing before you buy.
- Full feature access
- All AI model integrations
- Split-screen multitasking
- File uploads and parsing
- Custom agents and prompts
- Data is not saved between sessions
Lifetime License
Most Popular€99€149
One-time purchase for unlimited access, lifetime updates, and complete data control.
- Everything in Free
- Data persistence across sessions
- MultitaskAI Cloud sync
- Cross-device synchronization
- 5 device activations
- Lifetime updates
- Self-hosting option
- Priority support
Loved by users worldwide
See what our community says about their MultitaskAI experience.
Finally found a ChatGPT alternative that actually respects my privacy. The split-screen feature is a game changer for comparing models.
Sarah
Been using this for months now. The fact that I only pay for what I use through my own API keys saves me so much money compared to subscriptions.
Marcus
The offline support is incredible. I can work on my AI projects even when my internet is spotty. Pure genius.
Elena
Love how I can upload files and create custom agents. Makes my workflow so much more efficient than basic chat interfaces.
David
Self-hosting this was easier than I expected. Now I have complete control over my data and conversations.
Rachel
The background processing feature lets me work on multiple conversations at once. No more waiting around for responses.
Alex
Switched from ChatGPT Plus and haven't looked back. This gives me access to all the same models with way more features.
Maya
Finally found a ChatGPT alternative that actually respects my privacy. The split-screen feature is a game changer for comparing models.
Sarah
Been using this for months now. The fact that I only pay for what I use through my own API keys saves me so much money compared to subscriptions.
Marcus
The offline support is incredible. I can work on my AI projects even when my internet is spotty. Pure genius.
Elena
Love how I can upload files and create custom agents. Makes my workflow so much more efficient than basic chat interfaces.
David
Self-hosting this was easier than I expected. Now I have complete control over my data and conversations.
Rachel
The background processing feature lets me work on multiple conversations at once. No more waiting around for responses.
Alex
Switched from ChatGPT Plus and haven't looked back. This gives me access to all the same models with way more features.
Maya
Finally found a ChatGPT alternative that actually respects my privacy. The split-screen feature is a game changer for comparing models.
Sarah
Been using this for months now. The fact that I only pay for what I use through my own API keys saves me so much money compared to subscriptions.
Marcus
The offline support is incredible. I can work on my AI projects even when my internet is spotty. Pure genius.
Elena
Love how I can upload files and create custom agents. Makes my workflow so much more efficient than basic chat interfaces.
David
Self-hosting this was easier than I expected. Now I have complete control over my data and conversations.
Rachel
The background processing feature lets me work on multiple conversations at once. No more waiting around for responses.
Alex
Switched from ChatGPT Plus and haven't looked back. This gives me access to all the same models with way more features.
Maya
Finally found a ChatGPT alternative that actually respects my privacy. The split-screen feature is a game changer for comparing models.
Sarah
Been using this for months now. The fact that I only pay for what I use through my own API keys saves me so much money compared to subscriptions.
Marcus
The offline support is incredible. I can work on my AI projects even when my internet is spotty. Pure genius.
Elena
Love how I can upload files and create custom agents. Makes my workflow so much more efficient than basic chat interfaces.
David
Self-hosting this was easier than I expected. Now I have complete control over my data and conversations.
Rachel
The background processing feature lets me work on multiple conversations at once. No more waiting around for responses.
Alex
Switched from ChatGPT Plus and haven't looked back. This gives me access to all the same models with way more features.
Maya
Switched from ChatGPT Plus and haven't looked back. This gives me access to all the same models with way more features.
Maya
The sync across devices works flawlessly. I can start a conversation on my laptop and continue on my phone seamlessly.
James
As a developer, having all my chats, files, and agents organized in one place has transformed how I work with AI.
Sofia
The lifetime license was such a smart purchase. No more monthly fees, just pure productivity.
Ryan
Queue requests feature is brilliant. I can line up my questions and let the AI work through them while I focus on other tasks.
Lisa
Having access to Claude, GPT-4, and Gemini all in one interface is exactly what I needed for my research.
Mohamed
The file parsing capabilities saved me hours of work. Just drag and drop documents and the AI understands everything.
Emma
Switched from ChatGPT Plus and haven't looked back. This gives me access to all the same models with way more features.
Maya
The sync across devices works flawlessly. I can start a conversation on my laptop and continue on my phone seamlessly.
James
As a developer, having all my chats, files, and agents organized in one place has transformed how I work with AI.
Sofia
The lifetime license was such a smart purchase. No more monthly fees, just pure productivity.
Ryan
Queue requests feature is brilliant. I can line up my questions and let the AI work through them while I focus on other tasks.
Lisa
Having access to Claude, GPT-4, and Gemini all in one interface is exactly what I needed for my research.
Mohamed
The file parsing capabilities saved me hours of work. Just drag and drop documents and the AI understands everything.
Emma
Switched from ChatGPT Plus and haven't looked back. This gives me access to all the same models with way more features.
Maya
The sync across devices works flawlessly. I can start a conversation on my laptop and continue on my phone seamlessly.
James
As a developer, having all my chats, files, and agents organized in one place has transformed how I work with AI.
Sofia
The lifetime license was such a smart purchase. No more monthly fees, just pure productivity.
Ryan
Queue requests feature is brilliant. I can line up my questions and let the AI work through them while I focus on other tasks.
Lisa
Having access to Claude, GPT-4, and Gemini all in one interface is exactly what I needed for my research.
Mohamed
The file parsing capabilities saved me hours of work. Just drag and drop documents and the AI understands everything.
Emma
Switched from ChatGPT Plus and haven't looked back. This gives me access to all the same models with way more features.
Maya
The sync across devices works flawlessly. I can start a conversation on my laptop and continue on my phone seamlessly.
James
As a developer, having all my chats, files, and agents organized in one place has transformed how I work with AI.
Sofia
The lifetime license was such a smart purchase. No more monthly fees, just pure productivity.
Ryan
Queue requests feature is brilliant. I can line up my questions and let the AI work through them while I focus on other tasks.
Lisa
Having access to Claude, GPT-4, and Gemini all in one interface is exactly what I needed for my research.
Mohamed
The file parsing capabilities saved me hours of work. Just drag and drop documents and the AI understands everything.
Emma
The file parsing capabilities saved me hours of work. Just drag and drop documents and the AI understands everything.
Emma
Dark mode, keyboard shortcuts, and the clean interface make this a joy to use daily.
Carlos
Fork conversations feature is perfect for exploring different ideas without losing my original train of thought.
Aisha
The custom agents with specific instructions have made my content creation process so much more streamlined.
Thomas
Best investment I've made for my AI workflow. The features here put other chat interfaces to shame.
Zoe
Privacy-first approach was exactly what I was looking for. My data stays mine.
Igor
The PWA works perfectly on mobile. I can access all my conversations even when I'm offline.
Priya
Support team is amazing. Quick responses and they actually listen to user feedback for improvements.
Nathan
The file parsing capabilities saved me hours of work. Just drag and drop documents and the AI understands everything.
Emma
Dark mode, keyboard shortcuts, and the clean interface make this a joy to use daily.
Carlos
Fork conversations feature is perfect for exploring different ideas without losing my original train of thought.
Aisha
The custom agents with specific instructions have made my content creation process so much more streamlined.
Thomas
Best investment I've made for my AI workflow. The features here put other chat interfaces to shame.
Zoe
Privacy-first approach was exactly what I was looking for. My data stays mine.
Igor
The PWA works perfectly on mobile. I can access all my conversations even when I'm offline.
Priya
Support team is amazing. Quick responses and they actually listen to user feedback for improvements.
Nathan
The file parsing capabilities saved me hours of work. Just drag and drop documents and the AI understands everything.
Emma
Dark mode, keyboard shortcuts, and the clean interface make this a joy to use daily.
Carlos
Fork conversations feature is perfect for exploring different ideas without losing my original train of thought.
Aisha
The custom agents with specific instructions have made my content creation process so much more streamlined.
Thomas
Best investment I've made for my AI workflow. The features here put other chat interfaces to shame.
Zoe
Privacy-first approach was exactly what I was looking for. My data stays mine.
Igor
The PWA works perfectly on mobile. I can access all my conversations even when I'm offline.
Priya
Support team is amazing. Quick responses and they actually listen to user feedback for improvements.
Nathan
The file parsing capabilities saved me hours of work. Just drag and drop documents and the AI understands everything.
Emma
Dark mode, keyboard shortcuts, and the clean interface make this a joy to use daily.
Carlos
Fork conversations feature is perfect for exploring different ideas without losing my original train of thought.
Aisha
The custom agents with specific instructions have made my content creation process so much more streamlined.
Thomas
Best investment I've made for my AI workflow. The features here put other chat interfaces to shame.
Zoe
Privacy-first approach was exactly what I was looking for. My data stays mine.
Igor
The PWA works perfectly on mobile. I can access all my conversations even when I'm offline.
Priya
Support team is amazing. Quick responses and they actually listen to user feedback for improvements.
Nathan
2. API Gateway Implementation
Implementing an API gateway is a crucial API security best practice for protecting your backend services and ensuring a smooth experience for your users. An API gateway acts as a central point of entry for all API requests, similar to a reverse proxy. It intercepts incoming requests and handles essential cross-cutting concerns like authentication, authorization, rate limiting, and request routing, before forwarding them to the appropriate backend service. This centralized approach simplifies security management and provides a consistent interface for clients, shielding them from the complexities of your underlying microservices architecture.
A key benefit of using an API gateway is its ability to enforce security policies at a single point. Instead of implementing authentication and authorization logic in each microservice, the gateway handles these tasks, ensuring consistent security across all your APIs. This reduces code duplication and simplifies security updates. The gateway also decouples the client from the backend services, allowing you to refactor and modify your backend without impacting the client experience. This abstraction simplifies client integration and allows for greater flexibility in your architecture.
Features and Benefits:
- Centralized Authentication and Authorization: Secure your APIs by enforcing authentication and authorization policies at the gateway level.
- Rate Limiting and Throttling: Protect your backend from overload by controlling the rate of incoming requests.
- Request Validation: Validate incoming requests to ensure they conform to expected formats and prevent malicious requests from reaching your backend.
- Traffic Management: Route traffic to different backend services based on various criteria, enabling load balancing and A/B testing.
- Analytics and Monitoring: Gain insights into API usage and performance, allowing you to identify bottlenecks and optimize your services.
- Response Caching: Cache frequently accessed data at the gateway level to improve performance and reduce load on your backend services.
Pros:
- Single point for enforcing security policies
- Simplifies client integration
- Provides abstraction of backend services
- Enables consistent monitoring and analytics
Cons:
- Can become a single point of failure if not properly architected
- May introduce additional latency
- Requires expertise to configure properly
- Can become a performance bottleneck if not scaled appropriately
Examples:
- Amazon API Gateway: A fully managed service for creating, publishing, maintaining, monitoring, and securing REST, HTTP, and WebSocket APIs at any scale.
- Kong API Gateway: An open-source API gateway and microservices management layer built for hybrid and multi-cloud environments.
- Apigee Edge (Google Cloud): A platform for developing and managing APIs, providing features like security, analytics, and monetization.
- Microsoft Azure API Management: A hybrid, multi-cloud management platform for APIs across all environments.
Actionable Tips for Implementation:
- Implement Auto-Scaling: Ensure your API gateway can handle traffic spikes by configuring auto-scaling.
- Use Circuit Breakers: Prevent cascading failures by implementing circuit breakers to isolate failing services.
- Monitor Gateway Performance: Closely monitor gateway performance metrics to identify potential bottlenecks.
- Configure Timeouts: Prevent long-running requests from tying up resources by configuring appropriate timeouts.
- Request/Response Transformation: Standardize data formats by using request and response transformation capabilities.
When and Why to Use an API Gateway:
An API gateway is particularly beneficial when working with microservices architectures, where multiple backend services contribute to the overall application. It provides a unified entry point for clients and simplifies security management. It's also valuable for any application that requires robust security, rate limiting, and monitoring capabilities for its APIs. This approach is highly recommended as a core component of API security best practices because it addresses numerous security vulnerabilities and scalability challenges at a central point, simplifying management and improving the overall reliability of your API ecosystem. This secures your application and provides a better experience for your users.
3. TLS/SSL Encryption with Perfect Forward Secrecy
Implementing robust API security best practices is crucial for protecting sensitive data and maintaining user trust. Among these practices, Transport Layer Security (TLS), particularly with Perfect Forward Secrecy (PFS), stands out as a foundational element. This method safeguards data transmitted between clients and servers, ensuring confidentiality and integrity.
TLS/SSL, often used interchangeably (though SSL is now deprecated), establishes an encrypted connection, essentially creating a secure tunnel for API communication. This encryption prevents unauthorized access to data in transit, mitigating the risk of man-in-the-middle attacks where an attacker intercepts and potentially modifies communication. Beyond encryption, TLS also provides server authentication, assuring clients that they are communicating with the intended server and not a malicious imposter. This authentication relies on certificate-based trust chains, validating the server's identity.
Perfect Forward Secrecy (PFS) adds another layer of security by generating unique, ephemeral session keys for each communication session. Even if a server's private key is compromised in the future, past communication sessions remain secure because the session keys used for those sessions are not derivable from the compromised private key. This characteristic is crucial for long-term data protection and is a core component of modern API security best practices.
Features and Benefits:
- Data encryption in transit: Prevents unauthorized access to sensitive data during transmission.
- Server and client authentication: Verifies the identities of both parties involved in the communication.
- Data integrity verification: Ensures that the data transmitted hasn't been tampered with.
- Ephemeral session keys with PFS: Protects past sessions even if the server's private key is compromised.
- Certificate-based trust chains: Establishes a secure chain of trust for server authentication.
Pros:
- Prevents man-in-the-middle attacks: Secures the communication channel against eavesdropping and data manipulation.
- Ensures data confidentiality during transmission: Protects sensitive data from unauthorized access.
- Provides server authentication to clients: Confirms the server's legitimacy, preventing impersonation attacks.
- Protects against eavesdropping and tampering: Ensures data integrity and authenticity.
Cons:
- Certificate management overhead: Requires managing and renewing certificates, which can be complex.
- Slight performance impact due to handshake process: The initial TLS handshake adds a small overhead to the connection establishment.
- Requires regular certificate renewal: Certificates expire and need to be renewed periodically.
- Can be misconfigured resulting in security vulnerabilities: Incorrect configuration can weaken the security provided by TLS.
Examples of Successful Implementation:
- Cloudflare: Widely known for its implementation of TLS 1.3 with PFS, enhancing the security of websites and APIs.
- Let's Encrypt: A non-profit certificate authority that offers free, automated TLS certificates, making it easier for everyone to implement secure connections.
- Stripe API: Requires TLS 1.2 or higher for all API calls, demonstrating a strong commitment to API security.
Actionable Tips for Implementation:
- Use TLS 1.2 or higher and disable older, insecure protocols (SSL, TLS 1.0, TLS 1.1).
- Configure strong cipher suites that support PFS (e.g., those using Diffie-Hellman Ephemeral key exchange).
- Implement HTTP Strict Transport Security (HSTS) to enforce secure connections.
- Automate certificate renewal processes to avoid disruptions and maintain security.
- Consider using certificate pinning for high-security applications, though carefully manage its limitations.
- Regularly test your TLS configuration with tools like Qualys SSL Labs to identify and address vulnerabilities.
When and Why to Use TLS/SSL with PFS:
TLS/SSL with PFS should be considered a mandatory requirement for any API that handles sensitive data. This includes APIs used for financial transactions, healthcare information, user authentication, and any other scenario where data confidentiality and integrity are critical. By prioritizing TLS/SSL with PFS, you significantly enhance your API security posture and protect against a wide range of potential threats. This is a fundamental best practice for all AI professionals, developers, software engineers, and anyone building or consuming APIs. Failing to implement proper TLS/SSL with PFS can expose your API and users to serious security risks.
4. Comprehensive Input Validation and Sanitization
A crucial API security best practice, and number four on our list, is comprehensive input validation and sanitization. This acts as the first line of defense against malicious data entering your system. It involves rigorously checking all data received by your API endpoints to ensure it conforms to the expected format, type, and content, while simultaneously stripping out or neutralizing any potentially harmful elements. This proactive approach significantly strengthens your API security posture.
How it Works:
Input validation and sanitization works by implementing a series of checks and filters on incoming data. Think of it as a gatekeeper for your API. Before any data is allowed to pass through and be processed by your application, it's thoroughly inspected. If the data doesn't meet predefined criteria, it's either rejected entirely, or sanitized (cleaned) to remove any potentially harmful components. This helps prevent a wide range of attacks.
Features of Effective Input Validation and Sanitization:
- Schema Validation for Request Payloads: Using schemas (like JSON Schema or OpenAPI) to define the structure and data types expected in API requests. This ensures incoming data adheres to the defined structure.
- Type Checking and Format Validation: Verifying that data is of the correct type (e.g., integer, string, boolean) and follows the expected format (e.g., email address, date).
- Whitelist-based Input Filtering: Allowing only specific characters, patterns, or values through, effectively blocking anything unexpected. This is much safer than blacklisting, which tries to block known bad inputs and can be easily circumvented.
- Parameter Binding and Automatic Sanitization: Frameworks often offer tools to automatically bind input parameters to variables and sanitize them based on predefined rules.
- Context-Specific Encoding: Encoding data appropriately depending on where it's being used (e.g., HTML encoding for data displayed in a web page, URL encoding for data used in a URL).
Why This is a Crucial API Security Best Practice:
This practice deserves its place on the list because it's a fundamental security control. By blocking or neutralizing malicious input before it reaches your application logic, you prevent a multitude of attacks. Without it, your API is vulnerable to exploits like SQL injection, NoSQL injection, command injection, cross-site scripting (XSS), and business logic manipulation.
Pros:
- Prevents various injection attacks (SQL, NoSQL, OS command, etc.): This is the primary benefit, significantly hardening your API against common attack vectors.
- Reduces the attack surface: By limiting the accepted inputs, you reduce the possibilities for attackers to exploit vulnerabilities.
- Improves API reliability and data quality: Ensuring data consistency and integrity.
- Simplifies backend processing logic: By providing clean, validated data to your backend, you reduce the need for complex error handling and data cleaning logic.
Cons:
- Can introduce complexity to request processing: Implementing robust validation can add overhead.
- May require frequent updates as business needs change: API specifications and data formats can evolve, requiring adjustments to validation rules.
- Too strict validation might impact legitimate use cases: Overly restrictive rules can inadvertently block valid requests.
- Multiple validation layers can impact performance: If not implemented efficiently, multiple layers of validation can introduce noticeable latency.
Examples of Successful Implementation:
- Stripe API: Known for its rigorous JSON schema validation, ensuring all requests conform to their strict API specifications.
- GitHub API: Provides clear parameter validation and detailed error messages, guiding developers towards correct usage.
- Express-validator (Node.js): A popular middleware for Express.js applications that simplifies input validation.
Actionable Tips:
- Apply validation at all application layers, not just API entry points: Defense in depth is key. Don't rely solely on API gateway validation.
- Use schema validation libraries (JSON Schema, OpenAPI): Leverage existing tools for efficient and standardized validation.
- Implement context-specific output encoding for different data contexts: Prevent XSS vulnerabilities by encoding data appropriately.
- Validate not just data type, but also data range and content: Ensure data falls within acceptable bounds and doesn't contain malicious patterns.
- Return detailed validation errors to help developers, but avoid exposing system information: Provide helpful error messages without revealing internal details that could aid attackers.
Popularized By:
- OWASP API Security Project: A leading resource for API security best practices.
- JSON Schema organization: Defines the JSON Schema standard for data validation.
- OpenAPI Initiative: Promotes the OpenAPI specification for API design and documentation.
- AJV library for JSON Schema validation: A popular JavaScript library for implementing JSON Schema validation.
By implementing comprehensive input validation and sanitization, you significantly strengthen your API against a wide array of attacks, ensuring its reliability and protecting your valuable data. This is a cornerstone of any robust API security strategy and a critical best practice for all developers.
No spam, no nonsense. Pinky promise.
5. Rate Limiting and Throttling
Rate limiting and throttling are essential API security best practices that protect your APIs from abuse, overuse, and denial-of-service attacks. They work by controlling the number of requests a client can make to an API within a specific timeframe. This helps maintain service availability for legitimate users, ensures fair resource allocation, and can even reduce infrastructure costs. This practice is crucial for anyone developing and deploying APIs, making it a key element of any API security strategy.
How It Works:
Rate limiting and throttling function by setting limits on API requests. These limits can be implemented using various algorithms, like the "token bucket" or "leaky bucket" algorithms, which control the flow of requests. Each client is allocated a certain number of "tokens" within a given time window (e.g., 100 requests per minute). When a client makes a request, a token is consumed. If they run out of tokens, subsequent requests are rejected until the time window resets and tokens are replenished. Throttling, a broader term, encompasses similar techniques but may involve delaying requests rather than outright rejecting them.
Features:
- Request quotas per time window: Define the maximum number of requests allowed within a specific period (e.g., per second, minute, hour, or day).
- Token bucket or leaky bucket algorithms: These algorithms provide different mechanisms for managing request flow. Token bucket allows bursts of requests, while leaky bucket enforces a more consistent rate.
- Per-client, per-endpoint, or global limits: Flexibility to apply limits at different levels – per individual client, specific API endpoints, or across the entire API.
- Graduated response to excessive requests: Instead of immediately blocking, a graduated response can involve warnings, temporary slowdowns, or eventual blocking for increasingly excessive request rates.
- Clear rate limit headers and documentation: Providing clear communication about rate limits in the API documentation and using standard headers in responses (like
X-RateLimit-Limit,X-RateLimit-Remaining, andX-RateLimit-Reset) helps clients understand and respect the limits.
Pros:
- Protects against DoS and DDoS attacks: By limiting the number of requests from any single source, rate limiting prevents attackers from overwhelming the API.
- Prevents API abuse and scraping: Deters malicious actors from scraping data or abusing the API for unintended purposes.
- Ensures service stability during traffic spikes: Helps maintain API availability even during unexpected surges in user traffic.
- Encourages efficient API usage patterns: Clients are incentivized to optimize their API usage and avoid unnecessary requests.
Cons:
- Can impact legitimate high-volume users if not properly configured: Carefully consider the limits and provide mechanisms for legitimate users with high request needs.
- Complex implementation for distributed systems: Managing rate limits across multiple servers requires careful coordination and potentially specialized infrastructure components.
- Requires careful tuning to balance security and usability: Finding the right balance between preventing abuse and allowing legitimate usage requires testing and adjustments.
- May require additional infrastructure components: Distributed rate limiting may necessitate using technologies like Redis or other distributed caching systems.
Examples of Successful Implementation:
- GitHub API: GitHub employs clear rate limiting with comprehensive documentation and informative headers in responses, making it easy for developers to understand the limits and adjust their usage accordingly.
- Twitter API: Twitter utilizes tiered rate limits based on authentication level, providing different levels of access based on user needs.
- Cloudflare: Cloudflare offers rate-limiting services for web applications, protecting against malicious traffic and ensuring website availability.
Tips for Implementation:
- Document your rate limits clearly in API documentation: Inform users about the limits, how they are calculated, and what to expect.
- Return rate limit information in response headers: Use standard headers like
X-RateLimit-Limit,X-RateLimit-Remaining, andX-RateLimit-Resetto provide real-time feedback to clients. - Use 429 (Too Many Requests) status code with Retry-After header: When a client exceeds the rate limit, return the appropriate status code (429) and include a
Retry-Afterheader indicating when they can retry. - Implement exponential backoff for clients: Encourage clients to progressively increase the time between retries when encountering rate limits to avoid further overloading the API.
- Consider different limits for different endpoints based on resource cost: Set limits based on the computational cost of each endpoint to optimize resource allocation.
- Use Redis or similar distributed stores for rate limit counters in distributed systems: For robust rate limiting in distributed environments, leverage technologies like Redis.
Learn more about Rate Limiting and Throttling
This aspect of API security deserves its place in the list of best practices because it directly addresses several critical concerns: preventing abuse, ensuring availability, and promoting fair usage. By implementing rate limiting and throttling, you're proactively protecting your API from a wide range of potential problems and ensuring a positive experience for all legitimate users. For AI professionals, software engineers, and entrepreneurs alike, understanding and implementing these practices are vital for building robust and secure APIs.
6. Security Headers and CORS Configuration
Security headers and proper Cross-Origin Resource Sharing (CORS) configuration are crucial API security best practices. They establish vital browser security boundaries, protecting both API consumers and providers. These HTTP headers act as instructions for browsers, dictating how they should handle content, restrict cross-origin requests, and prevent common web attacks like clickjacking, cross-site scripting (XSS), and information disclosure. By implementing robust security headers and a well-defined CORS policy, you add a critical layer of defense to your API, ensuring its integrity and protecting sensitive data. This makes them essential for any comprehensive API security strategy.

Security headers work by providing specific directives to the browser on how to handle the API response. For example, the Content-Security-Policy (CSP) header tells the browser which sources of content are allowed to be loaded, effectively mitigating XSS attacks. The X-Frame-Options header prevents clickjacking by controlling whether the API response can be embedded in an iframe. CORS, on the other hand, governs which origins are permitted to make cross-origin requests to the API. By specifying allowed origins in the Access-Control-Allow-Origin header, you prevent unauthorized access to your API resources from malicious websites.
Features and Benefits:
- Content-Security-Policy (CSP) controls: Define legitimate sources of content, mitigating XSS attacks.
- Cross-Origin Resource Sharing (CORS) rules: Control which websites can access your API, preventing unauthorized cross-origin requests.
- X-Content-Type-Options enforcement: Prevents MIME-sniffing vulnerabilities.
- X-Frame-Options protection: Mitigates clickjacking attempts.
- Strict-Transport-Security (HSTS) policy: Enforces HTTPS connections, protecting against man-in-the-middle attacks.
Pros:
- Provides defense in depth against browser-based attacks.
- Prevents unauthorized cross-origin access to API resources.
- Relatively easy to implement by adding headers to HTTP responses.
- Effectively mitigates XSS and clickjacking attacks.
Cons:
- Requires careful configuration to avoid breaking legitimate functionality. Incorrectly configured headers can block legitimate requests.
- Overly permissive CORS can introduce security vulnerabilities if wildcards are used indiscriminately.
- Some older browsers may have compatibility issues with certain headers.
- Security headers can be overlooked during API development due to their behind-the-scenes nature.
Examples of Successful Implementations:
- Google's API Platform: Known for its strict CSP and CORS implementation, ensuring only authorized access.
- PayPal API Gateway: Utilizes comprehensive security headers to protect sensitive financial data.
- Mozilla's Observatory Service: Encourages and provides guidance on proper header usage.
Actionable Tips:
- Specific Origins for CORS: Set
Access-Control-Allow-Originto specific origins, avoiding the wildcard (*) to prevent unauthorized access. - Strict CSP: Implement a strict Content-Security-Policy to limit the sources of allowed content and minimize XSS risks.
- Prevent MIME-Sniffing: Always use
X-Content-Type-Options: nosniffto prevent the browser from misinterpreting content types. - Block Iframing: Set
X-Frame-Options: DENYfor API responses to prevent clickjacking attacks. - Enforce HTTPS: Include
Strict-Transport-Securitywith a longmax-ageto enforce HTTPS connections and improve security. - Utilize Scanning Tools: Consider using security header scanning tools like Mozilla Observatory to identify and address potential weaknesses in your header configuration.
When and Why to Use This Approach:
Security headers and CORS configuration should be implemented from the very beginning of API development. They are fundamental security best practices for protecting both your API and its consumers from a range of browser-based attacks. By proactively configuring these headers, you significantly reduce the risk of vulnerabilities related to XSS, clickjacking, and unauthorized data access. This approach is vital for any API exposed to the web and especially crucial when dealing with sensitive user data.
7. API Monitoring and Logging: A Cornerstone of API Security Best Practices
API monitoring and logging is a crucial element of API security best practices, ensuring the confidentiality, integrity, and availability of your APIs. It involves systematically tracking, recording, and analyzing API traffic and behavior. This practice provides valuable insights into how your APIs are used, allowing you to detect security incidents, troubleshoot performance bottlenecks, ensure compliance with regulatory requirements, and optimize API performance. By proactively identifying and addressing potential issues, you maintain a robust security posture and ensure a positive user experience.
This approach works by collecting various data points related to API activity, such as request and response times, error rates, request payloads, and user authentication details. This data is then aggregated, analyzed, and visualized to identify trends, anomalies, and potential security threats. Think of it as a surveillance system for your APIs, constantly watching for suspicious activity and providing you with the information you need to take action.
Features of Effective API Monitoring and Logging:
- Real-time Security Monitoring: Constantly monitors API traffic for malicious activity, allowing for immediate response to threats.
- Anomaly Detection: Identifies unusual patterns in request traffic that might indicate attacks or other issues.
- Comprehensive Audit Logs: Records detailed information about API activity for compliance and forensic analysis.
- Performance Metrics Tracking: Monitors API performance metrics like latency and throughput for optimization.
- Automated Alerts: Triggers alerts for suspicious activities, allowing for proactive intervention.
- Log Aggregation and Analysis: Combines logs from multiple sources for centralized analysis and reporting.
Pros:
- Early Detection of Attacks and Anomalies: Proactive identification of security threats prevents significant damage.
- Forensic Evidence for Incident Investigation: Detailed logs provide crucial evidence for understanding and resolving security incidents.
- Compliance with Regulatory Requirements: Comprehensive logging supports compliance with industry regulations.
- Insights for API Improvement and Optimization: Usage patterns and performance data inform API optimization efforts.
Cons:
- Large Data Volumes: Can generate significant amounts of data, requiring appropriate storage and management solutions.
- Privacy Concerns: Excessive data collection can raise privacy concerns, requiring careful data handling practices.
- Investment in Infrastructure: Implementing a comprehensive monitoring solution requires investment in infrastructure and tools.
- False Positives: Incorrectly triggered alerts (false positives) can lead to alert fatigue and potentially missed genuine threats.
Examples of Successful Implementations:
- Datadog's API Security Monitoring Solution: Offers a comprehensive platform for monitoring API activity, detecting anomalies, and managing security threats.
- ELK Stack (Elasticsearch, Logstash, Kibana): Provides a powerful open-source solution for collecting, processing, and visualizing API logs.
- Splunk's API Monitoring Capabilities: Offers enterprise-grade API monitoring and security solutions for large organizations.
Actionable Tips for Implementation:
- Log Enough Context: Include sufficient information in logs to provide valuable insights, but avoid logging sensitive data like passwords or API keys.
- Structured Logging: Use consistent formats for logs to facilitate analysis and automation.
- Correlation IDs: Implement correlation IDs to track individual requests across distributed systems.
- Alerts for Unusual Patterns: Set up alerts for deviations from established baselines or known attack signatures.
- Baseline Metrics: Establish baseline metrics to understand normal API behavior and identify anomalies.
- Tamper-Proof Logs: Ensure logs are tamper-proof for compliance and forensic investigations.
- Log Rotation and Retention Policies: Implement appropriate log rotation and retention policies to manage storage and comply with regulations.
Learn more about API Monitoring and Logging
API Monitoring and Logging deserves its place on this list because it’s a foundational element of a robust API security strategy. It provides the visibility and insights necessary to understand API usage, detect and respond to security threats, and continuously improve API performance and reliability. For developers, AI professionals, and tech-savvy entrepreneurs alike, implementing these practices is essential for securing their APIs and protecting valuable data. By following the tips and considering the examples provided, you can implement effective API monitoring and logging to protect your APIs and ensure their long-term success.
8. JWTs and Token-Based Security
JWTs (JSON Web Tokens) are a crucial component of modern API security best practices, offering a robust and efficient way to manage authentication and authorization in your applications. They are digitally signed tokens used to securely transmit information between parties, essentially acting as a digital passport for your users. This approach significantly improves upon traditional session-based authentication, particularly in the context of distributed systems and microservices architectures.
How JWTs Work:
A JWT is a compact, self-contained string consisting of three parts separated by dots:
- Header: Contains information about the token type (JWT) and the hashing algorithm used (e.g., HS256, RS256).
- Payload: Contains the claims, which are statements about an entity (typically the user) and additional data. These claims can include user ID, email, role, expiration time, and other relevant information.
- Signature: Generated by cryptographically signing the header and payload using a secret key. This ensures the token's integrity, verifying that it hasn't been tampered with.
When a user successfully authenticates, the API issues a JWT. The user then includes this token in the authorization header (typically as a "Bearer" token) of subsequent requests. The API validates the token's signature and extracts the claims to authorize the user's access to resources. This stateless approach eliminates the need for the API to store session information, making it highly scalable and suitable for distributed environments.
Why Use JWTs for API Security?
JWTs earn their place among API security best practices due to several key advantages:
- Stateless Authentication and Authorization: Eliminates the need for server-side session storage, simplifying development and improving scalability.
- Enhanced Security: Cryptographic signing ensures token integrity, preventing tampering.
- Improved Performance: Reduces database lookups for session validation, leading to faster response times.
- Cross-Domain Functionality: Facilitates seamless single sign-on (SSO) across different domains.
- Microservices Compatibility: Ideal for distributed architectures, enabling secure communication between services.
Pros and Cons of JWTs:
Pros:
- Reduces database lookups for session validation.
- Works well in distributed and microservices architectures.
- Contains all necessary authorization information.
- Simplifies cross-domain authentication.
- Standardized and widely supported.
Cons:
- Cannot be invalidated before expiration without additional infrastructure (e.g., a blacklist or revocation system).
- Token size increases with more claims.
- Requires careful implementation to avoid security vulnerabilities.
- Token theft remains a risk if not properly secured.
Examples of Successful JWT Implementations:
- Auth0: A popular identity management platform that utilizes JWTs for secure authentication and authorization.
- AWS Cognito: A cloud-based user directory and identity provider that leverages JWTs for user authentication.
- Firebase Authentication: Google's backend-as-a-service platform uses JWT-based auth tokens for securing user access.
Actionable Tips for Implementing JWTs:
- Keep tokens short-lived (15-60 minutes): Minimizes the impact of potential token theft.
- Implement token refresh mechanisms: Allows users to stay logged in without needing to re-authenticate frequently.
- Store tokens securely (HttpOnly cookies for web apps): Prevents client-side JavaScript from accessing the token, mitigating XSS attacks.
- Validate all aspects of tokens (signature, expiration, issuer, audience): Ensures that the token is valid and intended for your API.
- Use strong signature algorithms (RS256 preferred over HS256 for scalability): Provides stronger security and better scalability compared to symmetric algorithms.
- Include only necessary claims to minimize token size: Improves performance and reduces bandwidth consumption.
- Consider a token blacklist/revocation mechanism for high-security applications: Allows you to invalidate compromised tokens before their expiration.
By following these best practices, you can effectively leverage JWTs to enhance the security and scalability of your APIs, making them a vital part of your overall API security strategy. They are a powerful tool for managing authentication and authorization in modern applications, and their widespread adoption highlights their effectiveness in securing APIs in diverse environments.
API Security Best Practices Comparison
| Best Practice | Implementation Complexity 🔄 | Resource Requirements ⚡ | Expected Outcomes 📊 | Ideal Use Cases 💡 | Key Advantages ⭐ |
|---|---|---|---|---|---|
| OAuth 2.0 and OpenID Connect Authentication | High - requires security expertise | Moderate - backend token management | Secure, scoped, token-based access control with delegated authorization | Secure API access, third-party integrations, centralized auth | Fine-grained access control; standardized & widely adopted |
| API Gateway Implementation | Moderate to High - configuration intensive | High - infrastructure and scaling | Centralized security, routing, rate limiting, analytics | Microservices architecture, unified API management | Single security point; simplifies client integration |
| TLS/SSL Encryption with Perfect Forward Secrecy | Moderate - requires certificate management | Low to Moderate - certificate and config setup | Encrypted, authenticated API communications with forward secrecy | All API communications requiring confidentiality and integrity | Prevents MitM attacks; ensures data confidentiality |
| Comprehensive Input Validation and Sanitization | Moderate - schema design and updates | Low to Moderate - validation libraries usage | Improved data quality; prevention of injection and logic attacks | APIs accepting complex input; security-first design | Reduces attack surface; improves stability |
| Rate Limiting and Throttling | Moderate - requires tuning and infrastructure | Moderate to High - depends on scale | Protection against abuse, DoS; service stability | Public APIs, high traffic environments | Protects resources; encourages fair usage |
| Security Headers and CORS Configuration | Low - HTTP header setup | Low - configuration only | Mitigation of browser-based attacks; controlled cross-origin access | Web APIs with browser clients | Easy to implement; prevents XSS and clickjacking |
| API Monitoring and Logging | Moderate - setup of logging & alerts | Moderate to High - storage and analysis | Early threat detection, compliance, operational insights | Security-sensitive, high availability APIs | Forensic evidence; anomaly detection; compliance support |
| JWTs and Token-Based Security | Moderate - cryptography and token management | Moderate - token validation & storage | Stateless authentication; simplified distributed system auth | Microservices, cross-domain authentication | Reduces session lookups; standardized token format |
Level Up Your API Security
Implementing robust API security is no longer a luxury but a necessity in today's interconnected digital landscape. Throughout this article, we've explored some of the most crucial API security best practices, ranging from fundamental concepts like TLS/SSL encryption and input validation to more advanced strategies like implementing OAuth 2.0, JWTs, and leveraging API gateways. By mastering these core principles, you can effectively safeguard your APIs against common vulnerabilities and protect sensitive data from unauthorized access.
Let’s recap the key takeaways for reinforcing your API security: strong authentication mechanisms like OAuth 2.0 and OpenID Connect, employing a robust API gateway, encrypting traffic with TLS/SSL and Perfect Forward Secrecy, validating and sanitizing all inputs, implementing rate limiting and throttling, configuring security headers and CORS settings, and diligently monitoring and logging API activity. Each of these API security best practices plays a vital role in building a comprehensive security strategy.
Taking these next steps will help you put these API security best practices into action: audit your existing APIs for potential vulnerabilities, prioritize implementing the recommendations discussed in this article, and explore tools that can assist you in managing API security more effectively.
By prioritizing API security best practices, you not only protect your data and systems but also build trust with your users. A secure API ecosystem is essential for fostering innovation, enabling seamless integrations, and driving business growth. Whether you're an AI professional working with LLMs like ChatGPT or Google Gemini, a software engineer building the next big app, or a tech-savvy entrepreneur launching a startup, securing your APIs is paramount to your success. Start implementing these practices today and build a more secure future for your digital ventures.