API key security best practices: 8 Essential Tips
Learn 8 api key security best practices to protect your data. Secure key management, access control & monitoring for robust defense.
Protecting Your APIs in the Modern Landscape
APIs are the backbone of today's interconnected world. They power everything from the apps on our phones to complex AI platforms and large language models. This makes API security not just a good idea, but an absolute necessity. Your API keys are like the keys to your digital kingdom. Losing them can expose sensitive data, disrupt services, and damage your reputation.
API security has evolved significantly. We've moved beyond basic authentication to more advanced, multi-layered strategies. Effective API security now combines proactive measures, intelligent automation, and continuous monitoring. Think of it like protecting a castle – you need multiple layers of defense.
This list will guide you through eight best practices for securing your API keys in 2025 and beyond. We'll cover everything from automating key management to securing your network.
Automating Key Management
Automating key management is the first line of defense. This involves automatically generating, rotating, and revoking API keys. This reduces the risk of human error and makes it much harder for attackers to compromise your keys.
Implementing Granular Access Controls
Granular access controls allow you to define precisely who can access what. This principle of least privilege limits the potential damage from a compromised key. Only grant the necessary permissions required for each user or service.
Leveraging Advanced Threat Detection
Advanced threat detection tools use AI and machine learning to identify suspicious activity. This helps you catch attacks early and prevent major breaches.
Securing Your Underlying Network Infrastructure
Protecting your network is crucial. This includes firewalls, intrusion detection systems, and regular security audits. A strong network foundation makes it harder for attackers to reach your APIs in the first place.
Encrypting Data in Transit and at Rest
Encryption is essential for protecting sensitive data. Encrypting data both in transit and at rest ensures that even if data is intercepted, it remains unreadable without the proper decryption keys.
Using Multi-Factor Authentication (MFA)
MFA adds an extra layer of security by requiring multiple forms of authentication. This makes it much harder for attackers to gain access, even if they have compromised a password or API key.
Performing Regular Security Audits and Penetration Testing
Regular security audits and penetration testing help you identify vulnerabilities before attackers do. These tests simulate real-world attacks to find weaknesses in your API security.
Staying Up-to-Date with Security Best Practices
The threat landscape is constantly evolving. Staying informed about the latest threats and best practices is vital for maintaining robust API security.
1. Key Rotation Automation

Key rotation is the cornerstone of strong API security. It's the practice of regularly updating your API keys to lessen the impact of potential compromises. Think of it like changing your passwords regularly, but for your applications.
This involves systematically generating new keys and retiring old ones on a set schedule. This significantly reduces the risk of attackers using compromised credentials. Key rotation automation is crucial because it proactively addresses a major security risk, preventing long-term damage from leaked or stolen keys.
The increasing use of APIs and more sophisticated cyberattacks have made key rotation essential. Early API implementations often relied on static, long-lived keys. This created a significant vulnerability. Once a key was compromised, it could be exploited indefinitely. The move towards shorter-lived keys and automated rotation helps contain breaches and limit potential damage. You might be interested in: Our guide on API Integration.
Key Features of Automated Key Rotation
Here are some of the core features of key rotation automation:
Automated Rotation on a Regular Schedule: Keys are automatically generated and replaced based on a defined schedule (e.g., every 30, 60, or 90 days).
Gradual Transition Periods: Both old and new keys work simultaneously for a short overlap period, ensuring a smooth transition for client applications.
Integration with Key Management Systems: Integration with robust key management systems like Hashicorp Vault streamlines the entire rotation process and strengthens security.
Audit Logging of Rotation Events: Detailed logs of key rotations provide valuable information for auditing and security analysis.
Pros and Cons of Key Rotation Automation
Let's look at the advantages and disadvantages of implementing key rotation automation:
Pros:
Reduces the Impact of Compromised Keys: Minimizes the damage an attacker can inflict.
Limits Attacker Access Duration: Restricts the time a compromised key is valid.
Forces Regular Review of API Access Patterns: Provides opportunities to identify unusual activity and improve access control policies.
Complies with Security Frameworks: Meets the requirements of many security and compliance standards.
Cons:
Potential Integration Disruptions: If not implemented carefully, rotation can briefly disrupt integrations with client applications.
Requires Robust Management Systems: Effective rotation requires reliable key management systems.
Increased Operational Overhead: Setting up and maintaining automated rotation adds some operational work.
Client Application Updates: Client applications need to be designed to handle key updates smoothly.
Real-World Examples of Key Rotation
Here are a few real-world examples of platforms using key rotation:
AWS IAM: Automatically rotates service credentials.
Google Cloud Platform: Offers key rotation for service accounts.
Stripe: Implements forced API key rotation for PCI compliance.
GitHub: Employs an automated personal access token expiration system.
Tips for Implementing Key Rotation
Here are some tips for implementing key rotation effectively:
Determine Rotation Frequency: Base your rotation schedule on the sensitivity of the data accessed by the API key (30-90 days is common).
Utilize Automation Tools: Use tools like Hashicorp Vault to automate the process.
Implement Overlap Periods: Allow both old and new keys to work during a transition period.
Communicate with Clients: Inform clients in advance of upcoming rotations.
Maintain Key Version History: Keep detailed records of key versions for troubleshooting and auditing.
By implementing key rotation automation, you significantly improve the security of your APIs and protect your data from potential threats.
Get started with your lifetime license
Enjoy unlimited conversations with MultitaskAI and unlock the full potential of cutting-edge language models—all with a one-time lifetime license.
Demo
Free
Try the full MultitaskAI experience with all features unlocked. Perfect for testing before you buy.
- Full feature access
- All AI model integrations
- Split-screen multitasking
- File uploads and parsing
- Custom agents and prompts
- Data is not saved between sessions
Lifetime License
Most Popular€99€149
One-time purchase for unlimited access, lifetime updates, and complete data control.
- Everything in Free
- Data persistence across sessions
- MultitaskAI Cloud sync
- Cross-device synchronization
- 5 device activations
- Lifetime updates
- Self-hosting option
- Priority support
Loved by users worldwide
See what our community says about their MultitaskAI experience.
Finally found a ChatGPT alternative that actually respects my privacy. The split-screen feature is a game changer for comparing models.
Sarah
Been using this for months now. The fact that I only pay for what I use through my own API keys saves me so much money compared to subscriptions.
Marcus
The offline support is incredible. I can work on my AI projects even when my internet is spotty. Pure genius.
Elena
Love how I can upload files and create custom agents. Makes my workflow so much more efficient than basic chat interfaces.
David
Self-hosting this was easier than I expected. Now I have complete control over my data and conversations.
Rachel
The background processing feature lets me work on multiple conversations at once. No more waiting around for responses.
Alex
Switched from ChatGPT Plus and haven't looked back. This gives me access to all the same models with way more features.
Maya
Finally found a ChatGPT alternative that actually respects my privacy. The split-screen feature is a game changer for comparing models.
Sarah
Been using this for months now. The fact that I only pay for what I use through my own API keys saves me so much money compared to subscriptions.
Marcus
The offline support is incredible. I can work on my AI projects even when my internet is spotty. Pure genius.
Elena
Love how I can upload files and create custom agents. Makes my workflow so much more efficient than basic chat interfaces.
David
Self-hosting this was easier than I expected. Now I have complete control over my data and conversations.
Rachel
The background processing feature lets me work on multiple conversations at once. No more waiting around for responses.
Alex
Switched from ChatGPT Plus and haven't looked back. This gives me access to all the same models with way more features.
Maya
Finally found a ChatGPT alternative that actually respects my privacy. The split-screen feature is a game changer for comparing models.
Sarah
Been using this for months now. The fact that I only pay for what I use through my own API keys saves me so much money compared to subscriptions.
Marcus
The offline support is incredible. I can work on my AI projects even when my internet is spotty. Pure genius.
Elena
Love how I can upload files and create custom agents. Makes my workflow so much more efficient than basic chat interfaces.
David
Self-hosting this was easier than I expected. Now I have complete control over my data and conversations.
Rachel
The background processing feature lets me work on multiple conversations at once. No more waiting around for responses.
Alex
Switched from ChatGPT Plus and haven't looked back. This gives me access to all the same models with way more features.
Maya
Finally found a ChatGPT alternative that actually respects my privacy. The split-screen feature is a game changer for comparing models.
Sarah
Been using this for months now. The fact that I only pay for what I use through my own API keys saves me so much money compared to subscriptions.
Marcus
The offline support is incredible. I can work on my AI projects even when my internet is spotty. Pure genius.
Elena
Love how I can upload files and create custom agents. Makes my workflow so much more efficient than basic chat interfaces.
David
Self-hosting this was easier than I expected. Now I have complete control over my data and conversations.
Rachel
The background processing feature lets me work on multiple conversations at once. No more waiting around for responses.
Alex
Switched from ChatGPT Plus and haven't looked back. This gives me access to all the same models with way more features.
Maya
Switched from ChatGPT Plus and haven't looked back. This gives me access to all the same models with way more features.
Maya
The sync across devices works flawlessly. I can start a conversation on my laptop and continue on my phone seamlessly.
James
As a developer, having all my chats, files, and agents organized in one place has transformed how I work with AI.
Sofia
The lifetime license was such a smart purchase. No more monthly fees, just pure productivity.
Ryan
Queue requests feature is brilliant. I can line up my questions and let the AI work through them while I focus on other tasks.
Lisa
Having access to Claude, GPT-4, and Gemini all in one interface is exactly what I needed for my research.
Mohamed
The file parsing capabilities saved me hours of work. Just drag and drop documents and the AI understands everything.
Emma
Switched from ChatGPT Plus and haven't looked back. This gives me access to all the same models with way more features.
Maya
The sync across devices works flawlessly. I can start a conversation on my laptop and continue on my phone seamlessly.
James
As a developer, having all my chats, files, and agents organized in one place has transformed how I work with AI.
Sofia
The lifetime license was such a smart purchase. No more monthly fees, just pure productivity.
Ryan
Queue requests feature is brilliant. I can line up my questions and let the AI work through them while I focus on other tasks.
Lisa
Having access to Claude, GPT-4, and Gemini all in one interface is exactly what I needed for my research.
Mohamed
The file parsing capabilities saved me hours of work. Just drag and drop documents and the AI understands everything.
Emma
Switched from ChatGPT Plus and haven't looked back. This gives me access to all the same models with way more features.
Maya
The sync across devices works flawlessly. I can start a conversation on my laptop and continue on my phone seamlessly.
James
As a developer, having all my chats, files, and agents organized in one place has transformed how I work with AI.
Sofia
The lifetime license was such a smart purchase. No more monthly fees, just pure productivity.
Ryan
Queue requests feature is brilliant. I can line up my questions and let the AI work through them while I focus on other tasks.
Lisa
Having access to Claude, GPT-4, and Gemini all in one interface is exactly what I needed for my research.
Mohamed
The file parsing capabilities saved me hours of work. Just drag and drop documents and the AI understands everything.
Emma
Switched from ChatGPT Plus and haven't looked back. This gives me access to all the same models with way more features.
Maya
The sync across devices works flawlessly. I can start a conversation on my laptop and continue on my phone seamlessly.
James
As a developer, having all my chats, files, and agents organized in one place has transformed how I work with AI.
Sofia
The lifetime license was such a smart purchase. No more monthly fees, just pure productivity.
Ryan
Queue requests feature is brilliant. I can line up my questions and let the AI work through them while I focus on other tasks.
Lisa
Having access to Claude, GPT-4, and Gemini all in one interface is exactly what I needed for my research.
Mohamed
The file parsing capabilities saved me hours of work. Just drag and drop documents and the AI understands everything.
Emma
The file parsing capabilities saved me hours of work. Just drag and drop documents and the AI understands everything.
Emma
Dark mode, keyboard shortcuts, and the clean interface make this a joy to use daily.
Carlos
Fork conversations feature is perfect for exploring different ideas without losing my original train of thought.
Aisha
The custom agents with specific instructions have made my content creation process so much more streamlined.
Thomas
Best investment I've made for my AI workflow. The features here put other chat interfaces to shame.
Zoe
Privacy-first approach was exactly what I was looking for. My data stays mine.
Igor
The PWA works perfectly on mobile. I can access all my conversations even when I'm offline.
Priya
Support team is amazing. Quick responses and they actually listen to user feedback for improvements.
Nathan
The file parsing capabilities saved me hours of work. Just drag and drop documents and the AI understands everything.
Emma
Dark mode, keyboard shortcuts, and the clean interface make this a joy to use daily.
Carlos
Fork conversations feature is perfect for exploring different ideas without losing my original train of thought.
Aisha
The custom agents with specific instructions have made my content creation process so much more streamlined.
Thomas
Best investment I've made for my AI workflow. The features here put other chat interfaces to shame.
Zoe
Privacy-first approach was exactly what I was looking for. My data stays mine.
Igor
The PWA works perfectly on mobile. I can access all my conversations even when I'm offline.
Priya
Support team is amazing. Quick responses and they actually listen to user feedback for improvements.
Nathan
The file parsing capabilities saved me hours of work. Just drag and drop documents and the AI understands everything.
Emma
Dark mode, keyboard shortcuts, and the clean interface make this a joy to use daily.
Carlos
Fork conversations feature is perfect for exploring different ideas without losing my original train of thought.
Aisha
The custom agents with specific instructions have made my content creation process so much more streamlined.
Thomas
Best investment I've made for my AI workflow. The features here put other chat interfaces to shame.
Zoe
Privacy-first approach was exactly what I was looking for. My data stays mine.
Igor
The PWA works perfectly on mobile. I can access all my conversations even when I'm offline.
Priya
Support team is amazing. Quick responses and they actually listen to user feedback for improvements.
Nathan
The file parsing capabilities saved me hours of work. Just drag and drop documents and the AI understands everything.
Emma
Dark mode, keyboard shortcuts, and the clean interface make this a joy to use daily.
Carlos
Fork conversations feature is perfect for exploring different ideas without losing my original train of thought.
Aisha
The custom agents with specific instructions have made my content creation process so much more streamlined.
Thomas
Best investment I've made for my AI workflow. The features here put other chat interfaces to shame.
Zoe
Privacy-first approach was exactly what I was looking for. My data stays mine.
Igor
The PWA works perfectly on mobile. I can access all my conversations even when I'm offline.
Priya
Support team is amazing. Quick responses and they actually listen to user feedback for improvements.
Nathan
2. Environment-Based Access Controls
Protecting your API keys is paramount. Environment-based access controls are a critical part of a strong security strategy. This practice involves implementing different security controls and permissions for your API keys depending on where they’re used. These environments could be development, staging, or production. This segmentation ensures that a compromised key in a less secure environment, like development, won't cause problems in your live production environment.
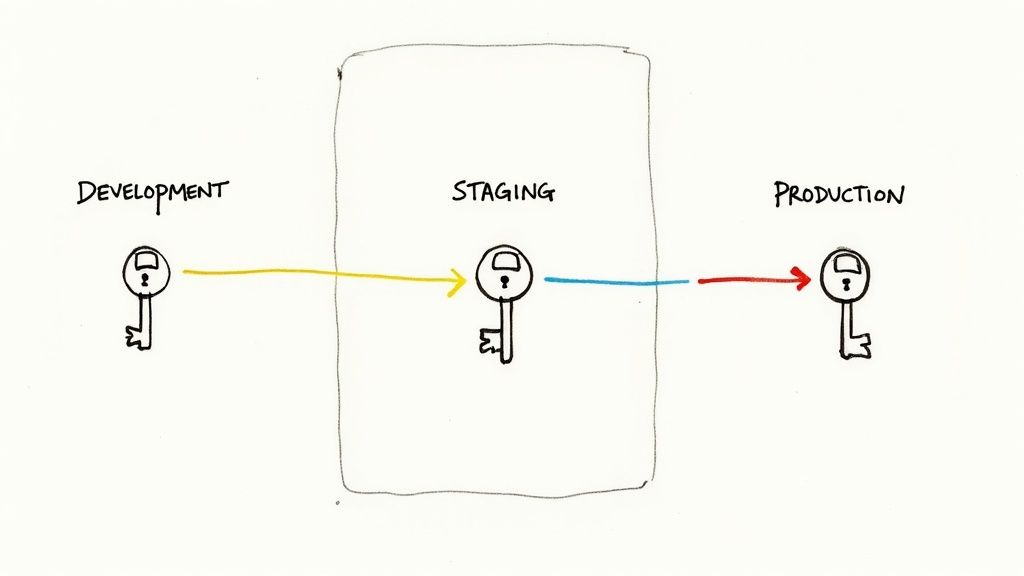
This approach has become more popular with the rise of DevOps and continuous integration/continuous delivery (CI/CD) pipelines. As software development cycles became faster and more complex, isolating different environments became crucial. Imagine a developer accidentally committing a development API key with broad permissions to a public repository like GitHub. Without environment-based controls, this could expose critical production resources.
Key Features of Environment-Based Access Controls
Here are some of the core features of environment-based access controls:
Environment-Specific API Keys: Different keys are generated for each environment. This prevents a key from one environment from being used in another.
Separate Key Stores: Each environment should maintain its own secure key store. This minimizes the impact if a single store is compromised.
Role-Based Permissions: Assign granular permissions based on the role and the environment. A developer might have full access in development, but only limited read-only access in production.
Environment Tagging and Metadata: Tagging keys with environment-specific metadata simplifies key management. This allows for easy identification and revocation.
Pros of Environment-Based Access Controls
Limits the Blast Radius: A compromised development key won't impact staging or production.
Enforces Separation of Concerns: Clear boundaries between environments encourage better code and security practices.
Flexible Security: Relaxed security in development speeds up iteration, while strict controls remain in production.
Supports Least Privilege: Grant only necessary permissions in each environment. This minimizes potential damage from a breach.
Cons of Environment-Based Access Controls
Increased Complexity: Managing multiple key sets and permissions can be more difficult.
Potential for Confusion: Developers working across environments need to track which key they're using.
Additional Infrastructure: Managing multiple key sets might require additional infrastructure and tools.
Potential Development Slowdown: Stricter controls might occasionally slow down development processes.
Real-World Examples
Many companies use environment-based access controls:
Stripe: Offers restricted API keys for different environments, ensuring test keys don't access live payment data.
Salesforce: Provides sandbox-specific API credentials for development and testing, separate from production.
Microsoft Azure: Uses resource-based access control across environments, offering granular control over access.
Twilio: Implements environment segmentation for API keys to isolate development, testing, and production communications.
Practical Tips for Implementation
Visual Indicators: Use color-coding or distinct naming (e.g.,
dev_api_key,prod_api_key) for environment-specific keys.Automate Key Provisioning: Integrate key generation and distribution into your CI/CD pipelines.
Infrastructure as Code (IaC): Manage permissions and key stores consistently across environments using IaC tools.
Consider Different Key Formats: Explore different formats or structures for keys in various environments.
You might be interested in: Our guide on Data Privacy Best Practices. Environment-based access controls are a fundamental way to limit damage from key compromises, ensuring the security of your application in all environments.
3. Granular Permission Scoping
Granular permission scoping is a critical API key security best practice. It centers around the principle of least privilege. Instead of giving API keys unrestricted access, this approach involves creating keys with very specific permissions. Each key only has access to the absolute minimum it needs. This significantly enhances your security.
Think of it like keycards for an office building. Instead of giving everyone a master key, you grant access only to relevant areas. A marketing team member might have access to the marketing department and common areas, but not the server room or finance department. This same principle applies to API keys.
Why Is Granular Permission Scoping Important?
A compromised API key with broad permissions can be devastating. It could grant unauthorized access to sensitive data, system configurations, or even control over critical functionalities. Granular permission scoping minimizes this risk by containing the potential damage.
Features that Enable Granular Permission Scoping:
Fine-grained access control: Control access at the resource and operation level. A key might only be allowed to read data from a specific database table.
Permission templates: Predefined permission sets for common use cases simplify the key creation process.
Time-bounded access scopes: Set expiration dates for keys or permissions.
Resource-path restrictions: Control access based on the resource path. A key could be limited to interacting with
/users/profile.Action-specific permissions: Grant permissions for specific actions like
read,write,delete, orexecute.
Pros of Granular Permission Scoping:
Minimizes Damage from Key Compromise: Contains the impact of a security breach.
Clear Visibility into Access: Provides a clear audit trail.
Easier Compliance: Simplifies adherence to regulatory requirements.
Prevents Accidental Destructive Operations: Reduces the risk of unintentional data loss.
Reduces Attack Surface: Limits potential entry points for attackers.
Cons of Granular Permission Scoping:
Initial Setup Complexity: Requires more upfront planning.
Potential for "Permission Creep": Keys might accumulate unnecessary permissions over time.
Increased Key Management Overhead: May require managing a larger number of keys.
Developer Friction: Developers might request excessive permissions.
Real-World Examples of Granular Permission Scoping:
Google Cloud IAM: Google Cloud IAM offers a highly granular permission system.
GitHub's Scoped Access Tokens: GitHub's scoped access tokens allow developers to grant specific permissions.
AWS IAM's Resource-Level Permissions: AWS IAM enables fine-grained control.
Okta's API Scopes for OAuth Tokens: Okta's API scopes define the specific data and actions an application can access.
Practical Tips for Implementation:
Start with Zero Permissions: Begin by granting no permissions and gradually add necessary ones.
Create Permission Templates: Develop standardized templates.
Regular Audits: Regularly review key permissions.
Request Process for Expansion: Implement a formal process for additional permissions.
Temporary Elevated Permissions: Use temporary elevated access for specific tasks.
Group Permissions by Business Function: Consider grouping permissions based on business functions.
Evolution and Popularization:
Granular permission scoping gained traction with the rise of the OAuth 2.0 framework. OAuth 2.0 allows users to grant limited access without sharing passwords. This, coupled with recommendations from organizations like NIST for stricter access controls, has made granular permission scoping a crucial security best practice.
By implementing granular permission scoping, you can significantly improve your API security. While it requires some upfront investment, the long-term benefits outweigh the initial effort.
4. Vault Systems For Secure Storage
Storing API keys securely is critical for protecting your applications and data. One of the most effective methods is using a vault system. These specialized tools safeguard sensitive information like API keys, offering a robust alternative to storing them in configuration files or code. This centralized approach provides a secure and manageable solution for handling API keys throughout their lifecycle.
Vault systems offer encrypted storage, granular access controls, and often include advanced features. These can include secret rotation, leasing, and comprehensive audit trails. This means your keys are encrypted at rest, access is tightly controlled based on authenticated identities, and you have a complete history of access.
Key Features of Vault Systems
Encrypted at-rest storage: Ensures keys remain unreadable even if the storage system is compromised.
Access control and authentication: Restricts access to authorized users and services.
Dynamic secret generation: Creates secrets on demand, reducing the risk of long-lived static keys.
Automatic key rotation: Regularly replaces keys, limiting the impact of potential compromise.
Audit logging: Tracks all key access activities for auditing and security analysis.
Temporary credential leasing: Provides time-limited access to secrets for enhanced security.
Pros
Centralized key management: Simplifies security policy enforcement and administration.
Eliminates hardcoding: Prevents credentials from being exposed in source code.
Comprehensive audit trails: Provides valuable insights for security monitoring and incident response.
Integration with identity providers: Leverages existing authentication systems for seamless access control.
Automated rotation: Reduces manual effort and improves security posture.
Cons
Dependency on the vault service: Introduces a new component that requires management and maintenance.
Potential single point of failure: Requires careful architecture and high-availability configuration.
Added latency: Retrieving secrets can introduce minor delays during application startup.
Operational overhead: Requires expertise to set up, configure, and manage effectively.
Real-World Examples
Netflix: Uses HashiCorp Vault for managing its infrastructure's secrets.
Capital One: Utilizes AWS Secrets Manager to secure its sensitive data.
Microsoft: Implements Azure Key Vault across its internal services and cloud offerings.
Financial Institutions: Widely use CyberArk's Conjur for robust secrets management in regulated environments.
Practical Tips For Implementation
High Availability: Implement a robust high-availability strategy to prevent service disruptions.
Environment Variables: Use environment variables to inject secrets retrieved from the vault into your applications.
CI/CD Integration: Integrate vault access into your CI/CD pipeline to automate secret deployment.
Automated Unsealing: Configure automated unsealing for non-production environments to simplify development workflows.
Granular Access Policies: Define separate access policies for human users and service accounts.
Periodic Key Rotation: Implement regular key rotation policies within the vault system.
Evolution and Popularization
The rise of DevOps and the increasing importance of cloud security have driven the adoption of vault systems. HashiCorp's Vault played a significant role in popularizing this approach, alongside cloud providers offering native key management services like AWS Secrets Manager and Azure Key Vault. The DevSecOps movement further emphasized the critical role of secrets management in secure software development lifecycles.
By adopting a vault system, you significantly improve your API key security and overall application security. The benefits of centralized management, automated rotation, and enhanced access controls outweigh the operational overhead, making it a vital best practice for any organization handling sensitive credentials.
No spam, no nonsense. Pinky promise.
5. Rate Limiting and Throttling
Rate limiting and throttling are essential for protecting your APIs. They prevent abuse, overuse, and potential attacks by restricting the number of API requests allowed within a specific timeframe. This is crucial for maintaining API availability and preventing denial-of-service attacks. It also protects against compromised API keys. This fundamental security practice directly impacts the reliability and security of your API.
Imagine a malicious actor obtains a valid API key. Without rate limiting, they could flood your API with thousands of requests per second. This could cripple your server and disrupt service for legitimate users. Rate limiting acts as a gatekeeper, preventing this abuse by enforcing usage limits.
How It Works
Rate limiting and throttling set quotas on API usage. These quotas can be defined in a few ways:
Request Count Limits: Limits the number of requests within a specific time window (e.g., 1000 requests per hour).
Concurrent Request Limitations: Restricts the number of simultaneous requests from a single key.
Usage-Based Throttling Tiers: Offers different request limits based on subscriptions or usage patterns.
Graduated Response Measures: Escalates restrictions based on abuse, from warnings to blocks or key revocation.
Custom Rate Limits: Sets specific limits for individual endpoints or operation types.
Benefits of Rate Limiting and Throttling
Properly implemented rate limiting and throttling offers several advantages:
Abuse Prevention: Limits damage from compromised API keys.
Backend Protection: Protects servers from resource exhaustion and denial-of-service attacks.
Anomaly Detection: Unusual usage can indicate malicious activity.
Cost Control: Helps manage costs for pay-per-use APIs.
Improved Client-Side Practices: Encourages efficient client-side caching.
Potential Drawbacks
While beneficial, there are some potential downsides:
Impact on Legitimate Users: Overly restrictive limits can hinder high-volume use cases.
Complexity: Requires careful configuration for security and usability.
Client-Side Handling: Clients need to handle rate limit responses and implement retries.
Support Overhead: Unexpectedly reached limits can lead to support requests.
Real-World Examples
Many companies use rate limiting:
Cloudflare: Offers rate limiting as part of their API management services. Cloudflare
GitHub: Implements rate limits based on authentication. GitHub
Twitter: Employs tiered rate limiting based on developer needs. Twitter
Stripe: Uses throttling for payment processing to prevent fraud. Stripe
Practical Tips for Implementation
Here are some tips for effective rate limiting:
Transparency: Include rate limit info (remaining requests, reset time) in API responses.
Exponential Backoff: Implement this in client libraries to handle rate limit errors.
Granular Control: Set different limits for different endpoints based on resource cost.
Business Impact Analysis: Consider the potential business impact when setting limits.
Notifications: Alert clients when approaching their usage limits.
Burst Handling: Handle legitimate traffic spikes without triggering limits.
Popularity and Evolution
Rate limiting is now standard practice due to the rise of public APIs and the need for resource management. The OWASP API Security Project recommends rate limiting. Rate limiting plugins in API gateways, such as Kong, have simplified implementation. Twitter's early adoption and documentation of their strategy also helped popularize the practice. Implementing these best practices will improve your API security and reliability.
6. Anomaly Detection and Monitoring
Protecting your APIs demands more than just robust authentication. You also need to proactively identify suspicious activity, even when API keys are used legitimately. This is where anomaly detection and monitoring comes into play. This essential security practice establishes a baseline of typical API usage and continuously checks for deviations. These deviations could point to a compromised key or malicious activity. It's a critical layer of defense against attacks that can slip past traditional security measures.
Anomaly detection systems utilize various techniques to spot unusual patterns in API usage. These include machine learning, statistical analysis, and rule-based systems. These systems create a behavioral baseline by observing the typical access patterns of each API key.
Factors considered include the frequency of requests, the types of data accessed, the user's geographic location, and the time of day the API is used. After establishing this baseline, the system constantly monitors API requests in real time. It triggers alerts for any activity that significantly deviates from the established norm.
Features and Benefits
Behavioral Baseline Establishment: The system learns the normal usage patterns for each individual API key.
Real-Time Monitoring: API requests and access patterns are continuously monitored.
Alert Systems: Security teams receive notifications about unusual activity, enabling a swift response.
Geographic Anomaly Detection: Access attempts from unexpected or unusual locations are flagged.
Unusual Endpoint Access Detection: The system identifies access to endpoints that are rarely used or not typically accessed.
Time-of-Day Access Pattern Monitoring: Deviations in access times are detected and flagged.
Pros and Cons of Anomaly Detection
Understanding both the advantages and disadvantages of anomaly detection systems is crucial for effective implementation.
Pros:
Detects compromised keys even with valid credentials.
Provides early warnings of potential attack attempts.
Adapts to evolving usage patterns.
Can automatically trigger protective actions, like blocking suspicious requests.
Creates audit trails for security investigations.
Cons:
Can generate false positives, requiring further investigation.
Needs adequate historical data to establish precise baselines.
Requires adjustments to handle legitimate changes in usage.
Often requires dedicated security personnel for management.
Real-World Examples
Several platforms offer robust anomaly detection capabilities:
AWS CloudTrail with GuardDuty for API anomaly detection
Datadog's Security Monitoring for API behavior analysis
Splunk's API security monitoring (widely implemented in major banks, with case studies often highlighted in their marketing)
Evolution and Popularity
The growth of cloud computing and increased API reliance have made anomaly detection more important than ever. Cloud Security Posture Management (CSPM) vendors have helped popularize these techniques. Frameworks like the MITRE ATT&CK framework, which catalogs adversarial tactics and techniques, also emphasize API abuse patterns. This highlights the growing need for robust detection systems. The financial services industry, particularly sensitive to fraud, has significantly driven the adoption of API anomaly detection.
Practical Tips for Implementation
Implementing anomaly detection effectively involves a strategic approach:
Start Simple: Begin with rule-based detection before implementing more complex machine learning-based systems.
Prioritize: Focus first on high-value or sensitive endpoints.
Gradual Response: Implement tiered response actions (alert, require additional verification, block).
Correlation: Correlate API activity with other security signals for a comprehensive view of your security landscape.
Incident Response: Develop a clear incident response plan for handling confirmed anomalies.
Continuous Improvement: Regularly review and adjust detection thresholds for optimal performance.
By implementing robust anomaly detection and monitoring, you significantly improve your API security posture. This helps protect your valuable data and systems from even the most sophisticated attacks.
7. Network-Level Security Controls
Protecting your API keys isn't just about keeping them secret. It's also about controlling where they can be used. Network-level security controls provide this extra layer of defense. Even if a key is compromised, these controls severely limit its usefulness to an attacker. Think of it like a bank vault: stealing the key doesn't get you past the bank's walls and security systems.
This approach restricts API key usage to specific IP addresses, ranges, or networks. It’s like a VIP pass: it grants access, but only to those on the approved guest list (your authorized networks). This greatly reduces the risk of unauthorized access from outside.
Features and Benefits
Network-level security uses several mechanisms to control access:
IP Address Whitelisting: Only certain IP addresses or ranges can make API calls. This is a common and relatively simple method.
VPC/VNET Service Endpoints: Cloud platforms like Amazon Web Services (AWS) and Microsoft Azure offer virtual private clouds (VPCs) or virtual networks (VNETs). Service endpoints allow private communication between your VPC/VNET and the API, bypassing the public internet.
Network Path Restrictions: Define specific routes or network paths allowed for API access. This offers more granular control than IP whitelisting.
Geographic Region Access Controls: Restrict access to specific geographic areas. This helps comply with data regulations or limit the scope of attacks.
Private Link Technologies: Cloud providers offer private link services (e.g., AWS PrivateLink, Azure Private Link) for private connections between your network and the API provider's network.
VPN or Direct Connect Requirements: Require a Virtual Private Network (VPN) or direct connect for API access. This ensures all communication uses a secure, private channel.
These features offer some key advantages:
Multi-Factor Security: Combines "something you have" (the API key) with "somewhere you are" (the authorized network).
Enhanced Security Against External Threats: Makes it much harder for attackers outside your network to use stolen keys.
Defense-in-Depth: Adds a network perimeter to your API security, supporting a layered security approach.
Compliance: Often meets regulatory requirements for sensitive data access, particularly in finance and healthcare.
Pros and Cons
Pros | Cons |
|---|---|
Multi-factor security | Difficult with dynamic IP addresses or cloud environments |
Strong protection against external attacks | Restricts legitimate mobile or distributed workforce access |
Supports defense-in-depth strategies | May require additional network infrastructure |
Often satisfies compliance requirements | Increases operational complexity for key management |
Real-World Examples
AWS PrivateLink: Access AWS services and partner services privately within your VPC, without exposing traffic to the public internet. Ideal for internal-only API access.
Google Cloud's VPC Service Controls: Defines a security perimeter around Google Cloud resources, including APIs, preventing data leaks and unauthorized access.
Azure Private Endpoints for API Management: Enables private access to your API Management instance from your Azure VNET, improving security and simplifying network setup.
Salesforce's IP Range Restrictions for API Access: Lets administrators restrict API access to specific IP addresses or ranges, improving security for Salesforce integrations.
Tips for Implementation
Tiered Restrictions: Implement different network restrictions based on data sensitivity.
Efficient IP Management: Use CIDR notation to manage IP ranges, especially in larger networks.
Cloud-Native Solutions: Use cloud provider private endpoints for smooth service-to-service communication in the cloud.
Dynamic IP Handling: Use tools like dynamic DNS or VPNs for users with dynamic IP addresses.
Emergency Access: Create emergency overrides for network restrictions to ensure business continuity.
Documentation: Document network dependencies and access rules for incident response and troubleshooting.
Evolution and Popularity
The growth of Zero Trust security models, combined with strict compliance needs in finance and healthcare, has made network-level security controls much more popular. Cloud services offering private connectivity, like AWS PrivateLink and Azure Private Link, have also boosted their adoption.
Network-level security controls are essential for any API security strategy. They offer a powerful way to reduce the risks of compromised API keys. By adding access control based on network location, you significantly strengthen your API security and protect valuable data.
8. Key Lifecycle Management
API key security isn't just about creating strong keys. It's also about managing them effectively throughout their lifecycle. Key lifecycle management is a systematic approach to handling API keys from creation to decommissioning. This involves formal procedures for requesting, approving, issuing, tracking, rotating, and revoking keys. This is crucial for minimizing security risks associated with outdated or forgotten credentials, ensuring your APIs remain secure and controlled.
A robust key lifecycle management system typically includes:
Formal key request and approval workflows: This ensures key creation aligns with business needs and isn't arbitrary.
Automatic key expiration dates: Setting expiration dates forces regular review and renewal, preventing stale or compromised keys.
Key ownership and purpose tracking: Knowing who owns a key and its purpose establishes accountability and helps with incident response.
Regular access reviews: Periodic reviews ensure only authorized personnel retain access.
Emergency revocation procedures: A clear revocation process for compromised keys limits damage from security breaches.
Centralized inventory of all active keys: A central repository provides a clear overview of all active keys for easier management and auditing.
Benefits of Robust Key Lifecycle Management
Implementing a robust key lifecycle management system offers significant advantages:
Prevents proliferation of forgotten/unused keys: Regular reviews and expirations eliminate unused keys, reducing the attack surface.
Ensures regular review of access needs: Access is granted on a need-to-know basis, minimizing unauthorized access risk.
Creates clear accountability for key usage: Tracking key ownership helps pinpoint the source of security issues.
Supports compliance reporting and audits: A documented lifecycle process simplifies compliance with industry standards and regulations like ISO 27001 and SOC 2.
Reduces security risks from orphaned credentials: Eliminating unused or forgotten keys prevents them from being misused.
Challenges of Implementing Key Lifecycle Management
While beneficial, key lifecycle management presents challenges:
Requires organizational discipline: The system relies on consistent adherence to defined processes.
Potential slowdown in initial development: Overly rigid processes can hinder early-stage development agility.
Needs ongoing enforcement and oversight: Regular monitoring and enforcement are crucial for continued effectiveness.
Creates administrative overhead: Managing key lifecycles requires dedicated resources and effort.
Real-world examples include Microsoft Azure API Management, Atlassian’s internal system, Salesforce’s framework, and systems used by financial institutions. These demonstrate the value of comprehensive key management. See also: Our guide on API Keys. The focus on security and compliance, driven by standards like the NIST Cybersecurity Framework, has further emphasized effective credential management.
Practical Tips for Implementation
Here's how to implement key lifecycle management:
Automatic expiration dates: Implement this for all new keys.
Key sensitivity policies: Create different policies based on key sensitivity.
Automated access reviews: Automate regular reviews with owner confirmation.
Key metadata: Maintain metadata about key purpose, owner, and approved use cases.
Employee transition procedures: Develop clear procedures for key transitions during employee changes.
Integrate with developer onboarding/offboarding: Include lifecycle management in these processes.
Key lifecycle management is a crucial API security best practice. It offers a structured, proactive approach to managing API keys, reducing security breach risks, and promoting a more secure API environment.
API Key Security: 8-Point Strategy Comparison
Strategy | 🔄 Complexity | ⚡ Resources | 📊 Outcomes | 💡 Ideal Use Cases | ⭐ Advantages |
|---|---|---|---|---|---|
Key Rotation Automation | Medium – automated but requires coordination | Requires key management systems and audit logging | Minimizes risk by regularly updating keys | Environments needing routine key updates | Reduces window of compromise and supports compliance |
Environment-Based Access Controls | High – managing multiple sets increases complexity | Needs dedicated infrastructure to segregate keys by environment | Restricts key use based on environment, limiting damage | Organizations with distinct dev/staging/production stages | Limits blast radius and enforces least privilege |
Granular Permission Scoping | High – detailed permission settings are complex | Requires robust monitoring and templating systems | Tightens access controls to minimize exposure | Integrations needing precise, operation-specific access | Minimizes attack surface and enhances audit and compliance measures |
Vault Systems for Secure Storage | High – integration of secure vault systems is challenging | Demands centralized, encrypted storage infrastructure | Enhances security via centralized key management | Enterprises that require encrypted and automated storage | Prevents hardcoding and supports automated rotation |
Rate Limiting and Throttling | Medium – tuning limits involves moderate complexity | Built into API gateways; minimal extra hardware/software is needed | Prevents abuse and resource exhaustion | High-traffic APIs and scenarios prone to request flooding | Protects backend services and mitigates DDoS risks |
Anomaly Detection and Monitoring | High – advanced setup with analytics and machine learning | Requires data analytics tools and continuous monitoring resources | Provides early detection of abnormal API usage | Security-sensitive environments demanding real-time alerts | Delivers proactive alerts and enables rapid incident response |
Network-Level Security Controls | Medium – configuring network restrictions is moderately complex | Involves network infrastructure and IP management tools | Blocks unauthorized access from non-approved networks | Scenarios with static IP ranges or controlled network access | Adds an extra layer of defense and enforces multi-factor security |
Key Lifecycle Management | Medium – formal workflows require ongoing discipline | Operational overhead through centralized key tracking systems | Ensures proper tracking, rotation, and revocation of keys | Enterprises with strict compliance and audit requirements | Prevents orphaned keys and maintains accountability |
Level Up Your API Security
Protecting your API keys is an ongoing process, not a one-time solution. By combining best practices—like key rotation automation, environment-based access controls, granular permission scoping, secure vault storage, rate limiting and throttling, anomaly detection, network-level security, and robust key lifecycle management—you significantly improve your overall API security.
Putting these concepts into action involves carefully assessing your specific needs and weaving these measures into your development and deployment workflows. Automating key rotation, for example, minimizes the window of vulnerability. Implementing the principle of least privilege through granular permissions limits the potential damage from compromised keys.
Using Vault systems provides an extra layer of protection by centralizing and encrypting your sensitive credentials. Actively monitoring API usage patterns and implementing anomaly detection can help identify and stop suspicious activity early on.
Staying Ahead of the Curve
Staying ahead of the curve requires continuous learning and adapting. The API security landscape is always changing, with new threats and vulnerabilities emerging regularly. Stay informed about new security trends. Regularly review and update your security practices to address new challenges.
Key Takeaways
Here’s a summary of key API security best practices:
Never embed keys directly in code. Always store them securely outside your application's codebase.
Rotate keys frequently. Automation makes this manageable and minimizes risk.
Implement the principle of least privilege. Grant only the necessary permissions for each key.
Monitor and analyze API activity. Quickly detect and respond to suspicious behavior.
Stay updated on the latest security best practices and trends. Continuous learning is essential.
In conclusion, API key security is critical for protecting your applications, data, and reputation. By taking a proactive and comprehensive approach to API key management, using these best practices, and staying informed about the latest developments, you can build a more secure and resilient foundation for your business.