8 API Key Management Best Practices for 2025
Enhance your API security with these 8 API key management best practices. Learn how to protect your sensitive data and prevent unauthorized access in 2025.
Protecting Your APIs in the Modern Landscape
APIs are essential for modern software. They power everything from simple mobile apps to complex AI platforms and machine learning models. Think of APIs as digital keys, granting access to valuable data and important system functions. But what if these keys fall into the wrong hands? The results can be devastating, leading to data breaches, service disruptions, financial losses, and damage to your reputation.
In the past, API security was often overlooked. Simple authentication methods left systems open to attack. As cyberattacks have become more sophisticated, the need for strong API key management has become crucial. Effective API security now demands a multi-layered strategy. It's no longer enough to have basic authentication. We need lifecycle management, access control, and ongoing monitoring.
What Makes Modern API Key Management Effective?
A truly effective modern API key management strategy provides granular control, minimizes vulnerabilities, and adapts to the constantly changing threat landscape. This means not only protecting your keys but also understanding who has access, what they have access to, and quickly detecting any suspicious activity.
This article explores eight key best practices for API key management. It's designed for AI professionals, developers, entrepreneurs, and anyone who works with APIs. The goal is to provide you with the knowledge you need to protect your systems and data.
Key Best Practices for API Security
- Encryption: Protecting sensitive data at rest and in transit.
- Access Control: Limiting access to API keys based on roles and responsibilities.
- Key Rotation: Regularly changing API keys to limit the impact of compromised keys.
- Anomaly Detection: Identifying unusual patterns of API usage that may indicate a security breach.
- Environmental Isolation: Separating development, testing, and production environments to contain potential security incidents.
- Logging and Auditing: Tracking API activity for security analysis and compliance.
- Two-Factor Authentication: Adding an extra layer of security to API key access.
- Automated Key Management: Using tools and systems to streamline and automate key management processes.
By understanding and implementing these best practices, you can build a comprehensive security framework for your APIs. You'll be well-equipped to handle the challenges of modern API security and keep your digital assets safe.
1. Encryption of API Keys at Rest and in Transit
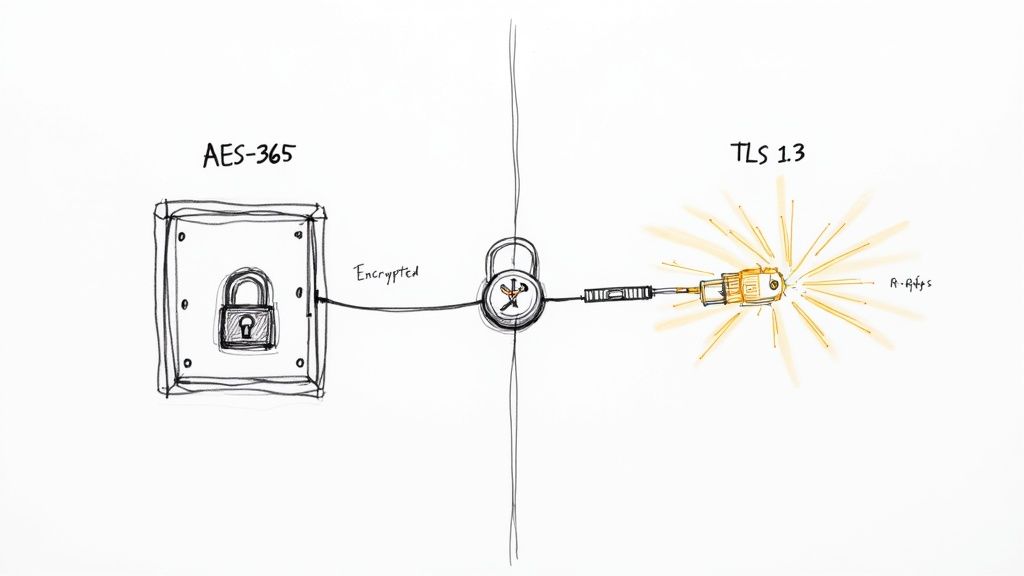
API keys are like passwords for your application or service. Losing them can have serious consequences, potentially exposing sensitive data and functionality. Therefore, encrypting API keys, both at rest and in transit, is paramount. This core security practice is fundamental to proper API key management. It protects your keys whether they are stored in a database (at rest) or being sent between systems (in transit).
Encryption scrambles the API key into an unreadable format. This renders it useless to anyone without the decryption key. This crucial security layer significantly reduces the risk of exposure, even if your systems are compromised. Think of it like a burglar breaking into a safe: if the contents are encrypted, the stolen data is meaningless.
How It Works and Why It Matters
At rest, encryption typically uses strong encryption algorithms, like AES-256, to encrypt the API keys stored in databases, configuration files, or other storage mechanisms. In transit, the industry standard is TLS 1.3. TLS 1.3 secures the connection between systems exchanging API keys. These protocols ensure end-to-end encryption of your sensitive credentials, protecting them from eavesdroppers or attackers intercepting network traffic.
The rise in cyberattacks makes encryption a non-negotiable security measure. Data breaches are common, and regulations like GDPR and HIPAA mandate the protection of sensitive information, making encryption essential for compliance.
Features and Benefits
- End-to-end encryption: Protects keys throughout their lifecycle.
- Industry-standard algorithms: Uses proven and robust encryption methods like AES-256 and TLS 1.3.
- Key rotation capabilities: Allows for regular key changes without disrupting encrypted storage.
Pros and Cons
Here's a quick overview of the advantages and disadvantages of encryption:
| Pros | Cons |
|---|---|
| Reduces risk of key exposure during breaches | Adds computational overhead to systems |
| Defense-in-depth key protection | Requires careful management of encryption keys |
| Complies with GDPR and HIPAA | Can introduce complexity in development workflows |
Real-World Examples and Implementation Tips
Several tools and services simplify encryption implementation:
- AWS Key Management Service (KMS): Provides a robust solution for encrypting API keys and other sensitive data in AWS cloud environments.
- HashiCorp Vault's Transit Secrets Engine: Offers encryption as a service, allowing you to encrypt and decrypt data without managing your own encryption keys.
- Google Cloud KMS: Similar to AWS KMS, this service helps protect API keys within the Google Cloud ecosystem.
Practical Tips
- Envelope encryption: Encrypt your API keys with a data key, then encrypt the data key with a master key stored securely.
- Environment-specific keys: Use different encryption keys for development, staging, and production environments.
- Regular audits: Periodically review your encryption implementation for vulnerabilities.
By prioritizing encryption of API keys at rest and in transit, you establish a strong foundation for API security, protecting your applications, data, and users. This proactive approach minimizes risks and reinforces trust in your services.
Get started with your lifetime license
Enjoy unlimited conversations with MultitaskAI and unlock the full potential of cutting-edge language models—all with a one-time lifetime license.
Demo
Free
Try the full MultitaskAI experience with all features unlocked. Perfect for testing before you buy.
- Full feature access
- All AI model integrations
- Split-screen multitasking
- File uploads and parsing
- Custom agents and prompts
- Data is not saved between sessions
Lifetime License
Most Popular€99€149
One-time purchase for unlimited access, lifetime updates, and complete data control.
- Everything in Free
- Data persistence across sessions
- MultitaskAI Cloud sync
- Cross-device synchronization
- 5 device activations
- Lifetime updates
- Self-hosting option
- Priority support
Loved by users worldwide
See what our community says about their MultitaskAI experience.
Finally found a ChatGPT alternative that actually respects my privacy. The split-screen feature is a game changer for comparing models.
Sarah
Been using this for months now. The fact that I only pay for what I use through my own API keys saves me so much money compared to subscriptions.
Marcus
The offline support is incredible. I can work on my AI projects even when my internet is spotty. Pure genius.
Elena
Love how I can upload files and create custom agents. Makes my workflow so much more efficient than basic chat interfaces.
David
Self-hosting this was easier than I expected. Now I have complete control over my data and conversations.
Rachel
The background processing feature lets me work on multiple conversations at once. No more waiting around for responses.
Alex
Switched from ChatGPT Plus and haven't looked back. This gives me access to all the same models with way more features.
Maya
Finally found a ChatGPT alternative that actually respects my privacy. The split-screen feature is a game changer for comparing models.
Sarah
Been using this for months now. The fact that I only pay for what I use through my own API keys saves me so much money compared to subscriptions.
Marcus
The offline support is incredible. I can work on my AI projects even when my internet is spotty. Pure genius.
Elena
Love how I can upload files and create custom agents. Makes my workflow so much more efficient than basic chat interfaces.
David
Self-hosting this was easier than I expected. Now I have complete control over my data and conversations.
Rachel
The background processing feature lets me work on multiple conversations at once. No more waiting around for responses.
Alex
Switched from ChatGPT Plus and haven't looked back. This gives me access to all the same models with way more features.
Maya
Finally found a ChatGPT alternative that actually respects my privacy. The split-screen feature is a game changer for comparing models.
Sarah
Been using this for months now. The fact that I only pay for what I use through my own API keys saves me so much money compared to subscriptions.
Marcus
The offline support is incredible. I can work on my AI projects even when my internet is spotty. Pure genius.
Elena
Love how I can upload files and create custom agents. Makes my workflow so much more efficient than basic chat interfaces.
David
Self-hosting this was easier than I expected. Now I have complete control over my data and conversations.
Rachel
The background processing feature lets me work on multiple conversations at once. No more waiting around for responses.
Alex
Switched from ChatGPT Plus and haven't looked back. This gives me access to all the same models with way more features.
Maya
Finally found a ChatGPT alternative that actually respects my privacy. The split-screen feature is a game changer for comparing models.
Sarah
Been using this for months now. The fact that I only pay for what I use through my own API keys saves me so much money compared to subscriptions.
Marcus
The offline support is incredible. I can work on my AI projects even when my internet is spotty. Pure genius.
Elena
Love how I can upload files and create custom agents. Makes my workflow so much more efficient than basic chat interfaces.
David
Self-hosting this was easier than I expected. Now I have complete control over my data and conversations.
Rachel
The background processing feature lets me work on multiple conversations at once. No more waiting around for responses.
Alex
Switched from ChatGPT Plus and haven't looked back. This gives me access to all the same models with way more features.
Maya
Switched from ChatGPT Plus and haven't looked back. This gives me access to all the same models with way more features.
Maya
The sync across devices works flawlessly. I can start a conversation on my laptop and continue on my phone seamlessly.
James
As a developer, having all my chats, files, and agents organized in one place has transformed how I work with AI.
Sofia
The lifetime license was such a smart purchase. No more monthly fees, just pure productivity.
Ryan
Queue requests feature is brilliant. I can line up my questions and let the AI work through them while I focus on other tasks.
Lisa
Having access to Claude, GPT-4, and Gemini all in one interface is exactly what I needed for my research.
Mohamed
The file parsing capabilities saved me hours of work. Just drag and drop documents and the AI understands everything.
Emma
Switched from ChatGPT Plus and haven't looked back. This gives me access to all the same models with way more features.
Maya
The sync across devices works flawlessly. I can start a conversation on my laptop and continue on my phone seamlessly.
James
As a developer, having all my chats, files, and agents organized in one place has transformed how I work with AI.
Sofia
The lifetime license was such a smart purchase. No more monthly fees, just pure productivity.
Ryan
Queue requests feature is brilliant. I can line up my questions and let the AI work through them while I focus on other tasks.
Lisa
Having access to Claude, GPT-4, and Gemini all in one interface is exactly what I needed for my research.
Mohamed
The file parsing capabilities saved me hours of work. Just drag and drop documents and the AI understands everything.
Emma
Switched from ChatGPT Plus and haven't looked back. This gives me access to all the same models with way more features.
Maya
The sync across devices works flawlessly. I can start a conversation on my laptop and continue on my phone seamlessly.
James
As a developer, having all my chats, files, and agents organized in one place has transformed how I work with AI.
Sofia
The lifetime license was such a smart purchase. No more monthly fees, just pure productivity.
Ryan
Queue requests feature is brilliant. I can line up my questions and let the AI work through them while I focus on other tasks.
Lisa
Having access to Claude, GPT-4, and Gemini all in one interface is exactly what I needed for my research.
Mohamed
The file parsing capabilities saved me hours of work. Just drag and drop documents and the AI understands everything.
Emma
Switched from ChatGPT Plus and haven't looked back. This gives me access to all the same models with way more features.
Maya
The sync across devices works flawlessly. I can start a conversation on my laptop and continue on my phone seamlessly.
James
As a developer, having all my chats, files, and agents organized in one place has transformed how I work with AI.
Sofia
The lifetime license was such a smart purchase. No more monthly fees, just pure productivity.
Ryan
Queue requests feature is brilliant. I can line up my questions and let the AI work through them while I focus on other tasks.
Lisa
Having access to Claude, GPT-4, and Gemini all in one interface is exactly what I needed for my research.
Mohamed
The file parsing capabilities saved me hours of work. Just drag and drop documents and the AI understands everything.
Emma
The file parsing capabilities saved me hours of work. Just drag and drop documents and the AI understands everything.
Emma
Dark mode, keyboard shortcuts, and the clean interface make this a joy to use daily.
Carlos
Fork conversations feature is perfect for exploring different ideas without losing my original train of thought.
Aisha
The custom agents with specific instructions have made my content creation process so much more streamlined.
Thomas
Best investment I've made for my AI workflow. The features here put other chat interfaces to shame.
Zoe
Privacy-first approach was exactly what I was looking for. My data stays mine.
Igor
The PWA works perfectly on mobile. I can access all my conversations even when I'm offline.
Priya
Support team is amazing. Quick responses and they actually listen to user feedback for improvements.
Nathan
The file parsing capabilities saved me hours of work. Just drag and drop documents and the AI understands everything.
Emma
Dark mode, keyboard shortcuts, and the clean interface make this a joy to use daily.
Carlos
Fork conversations feature is perfect for exploring different ideas without losing my original train of thought.
Aisha
The custom agents with specific instructions have made my content creation process so much more streamlined.
Thomas
Best investment I've made for my AI workflow. The features here put other chat interfaces to shame.
Zoe
Privacy-first approach was exactly what I was looking for. My data stays mine.
Igor
The PWA works perfectly on mobile. I can access all my conversations even when I'm offline.
Priya
Support team is amazing. Quick responses and they actually listen to user feedback for improvements.
Nathan
The file parsing capabilities saved me hours of work. Just drag and drop documents and the AI understands everything.
Emma
Dark mode, keyboard shortcuts, and the clean interface make this a joy to use daily.
Carlos
Fork conversations feature is perfect for exploring different ideas without losing my original train of thought.
Aisha
The custom agents with specific instructions have made my content creation process so much more streamlined.
Thomas
Best investment I've made for my AI workflow. The features here put other chat interfaces to shame.
Zoe
Privacy-first approach was exactly what I was looking for. My data stays mine.
Igor
The PWA works perfectly on mobile. I can access all my conversations even when I'm offline.
Priya
Support team is amazing. Quick responses and they actually listen to user feedback for improvements.
Nathan
The file parsing capabilities saved me hours of work. Just drag and drop documents and the AI understands everything.
Emma
Dark mode, keyboard shortcuts, and the clean interface make this a joy to use daily.
Carlos
Fork conversations feature is perfect for exploring different ideas without losing my original train of thought.
Aisha
The custom agents with specific instructions have made my content creation process so much more streamlined.
Thomas
Best investment I've made for my AI workflow. The features here put other chat interfaces to shame.
Zoe
Privacy-first approach was exactly what I was looking for. My data stays mine.
Igor
The PWA works perfectly on mobile. I can access all my conversations even when I'm offline.
Priya
Support team is amazing. Quick responses and they actually listen to user feedback for improvements.
Nathan
2. Principle of Least Privilege for API Keys
The Principle of Least Privilege (PoLP) is a core security concept. Applying it to API keys is essential for strong API security. This means each API key only has the permissions it needs for its specific job.
By limiting the scope of each key, you reduce the potential damage if a key is compromised. Imagine giving a store employee a key only to the stockroom, not the entire store. If that key is lost, the impact is contained.
This approach is critical because APIs are fundamental to many applications and services. A compromised API key with broad permissions could cause data breaches, service interruptions, or financial losses. PoLP helps minimize these risks.
Features that Support the Principle of Least Privilege
- Granular Permission Settings: Control exactly which API endpoints and operations each key can access.
- Role-Based Access Control (RBAC) Integration: Assign roles with predefined permission sets to API keys, simplifying management.
- Time-Bound or Context-Bound Permissions: Restrict access by limiting a key's validity to a specific time or situation.
Advantages of Using PoLP
- Reduced Attack Surface: Limiting each key's scope minimizes the damage from a security breach.
- Simplified Audits: Clearly defined key purposes make tracking API usage and finding suspicious activity easier.
- Improved Compliance: PoLP aligns with security frameworks like the NIST Cybersecurity Framework and the OWASP API Security Project.
Disadvantages of Using PoLP
- Administrative Overhead: Managing granular permissions takes careful planning and ongoing effort.
- Multiple Keys: You'll likely need several keys with specific permissions instead of one all-powerful key.
- Initial Analysis: Understanding the necessary permissions for each API interaction requires upfront analysis.
Real-World Use Cases
- Stripe: Create restricted API keys with access limited to specific resources (like customers or payments) and operations (like read-only access).
- AWS IAM: Offers fine-grained API access control through roles and policies. Define precisely which AWS services and actions a key can perform.
- GitHub: Personal Access Tokens (PATs) can be granted specific permissions to individual repositories, controlling access to your code.
Practical Implementation Tips
- Regular Audits: Check key permissions regularly. Revoke or update keys as needed.
- Separate Read/Write Keys: Create different keys for reading and writing data for added security.
- Document Key Purposes: Maintain clear documentation of the purpose and scope of each key.
- Just-in-Time Access: Grant access only when needed and revoke it afterward if possible.
Growing Importance of PoLP
The Principle of Least Privilege has been around for a long time. However, its use with API keys has become more important with the growth of cloud computing and API-driven systems. Frameworks like the NIST Cybersecurity Framework, Google's BeyondCorp, and the OWASP API Security Project highlight the importance of PoLP for API security. This increased focus, combined with growing awareness of API security risks, makes PoLP a best practice for any organization using APIs.
This principle is a cornerstone of a secure API strategy. Using the Principle of Least Privilege significantly improves your security and protects your data and services. It’s a vital step for anyone working with APIs.
3. Automated Key Rotation and Expiration
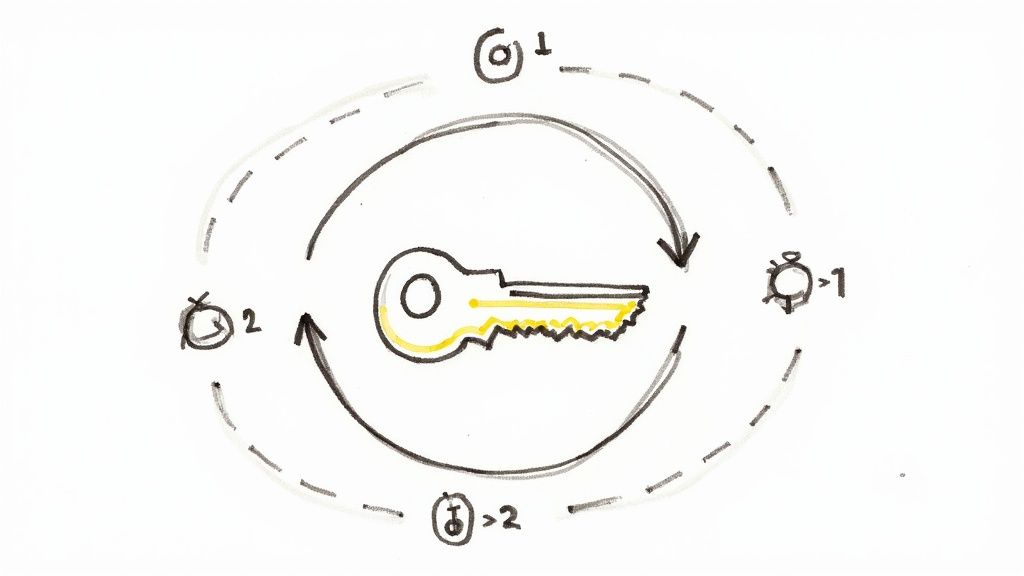
API keys are like passwords for your application's resources. Leaving them valid indefinitely presents a significant security risk. Automated key rotation and expiration is a critical best practice. It significantly reduces potential damage from compromised keys.
This involves implementing systematic, automated processes. These processes regularly rotate API keys and set appropriate expiration timelines. This limits the window of opportunity for attackers if keys are compromised. It also ensures keys don't remain active long after they're no longer needed.
Features of a Robust System
A robust key rotation and expiration system offers several key features:
- Scheduled key rotation processes: Automate the creation of new keys at specified intervals.
- Time-bound validity periods for API keys: Keys expire automatically after a set time.
- Automated creation and distribution of new keys: Streamline new key delivery to authorized users or systems.
- Graceful transition periods between old and new keys: Allow simultaneous function of old and new keys to prevent service interruptions.
Why is This Crucial?
Imagine a leaked API key. Without rotation and expiration, that key remains a permanent vulnerability. Automated rotation limits the leaked key's validity, mitigating potential damage.
This practice also enforces regular security audits of key usage. It creates natural opportunities to review and update permissions. This further limits the impact of potential breaches.
Pros and Cons of Automated Key Rotation
Here's a quick overview of the advantages and disadvantages:
| Pros | Cons |
|---|---|
| Reduces risk from undetected key compromise | Can cause service disruptions if not implemented carefully |
| Enforces regular security reviews | Requires solid automation and monitoring infrastructure |
| Facilitates permission updates | May increase operational complexity for developers |
Real-World Examples
Major cloud providers like AWS champion this best practice. AWS IAM automatically rotates access keys for service accounts. Azure Key Vault automates certificate rotation, and Cloudflare offers automatic expiration settings for API tokens. These examples highlight the widespread adoption of automated key rotation.
Practical Implementation Tips
Here are a few tips to ensure smooth implementation:
- Implement overlapping validity periods: This avoids disruptions during transitions.
- Set different rotation schedules based on key sensitivity: Rotate sensitive keys more frequently.
- Create alert systems for upcoming key expirations: Timely notifications ensure smooth transitions.
- Document and test regularly: Maintain clear documentation and test the process regularly.
- Use short-lived tokens with refresh mechanisms: Especially for sensitive operations.
The growing awareness of API security risks has made automated key rotation and expiration a top priority. Popular frameworks like the AWS Well-Architected Framework, Google Cloud Security Best Practices, and NIST Special Publication 800-57 promote its use. You can learn more in our guide on API Key Security Best Practices. By implementing this practice, developers and businesses can significantly improve their API security.
4. Secure Storage in Dedicated Secrets Management Solutions
Storing API keys directly in your code or configuration files presents a significant security risk. A far safer practice involves using dedicated secrets management solutions. These specialized systems offer encrypted storage, granular access controls, and comprehensive audit logging, and often integrate seamlessly with existing authentication systems. This centralized approach protects sensitive credentials and streamlines API key management.
This practice is crucial because it addresses a fundamental security vulnerability: exposed secrets. By storing API keys in a centralized, secure vault instead of scattering them throughout your codebase, you significantly reduce the potential attack surface. Features like versioning, access control lists, and audit logs provide a strong framework for managing and monitoring access to these critical credentials.
Key Features and Benefits of Secrets Management
Centralized Storage: All API credentials are kept in one secure location. This single source of truth simplifies management and minimizes the risk of keys being scattered across multiple systems.
Versioning and History: Track changes to secret values over time. This feature is invaluable for auditing and rollback scenarios.
Integrated Access Control: Fine-grained permissions ensure that only authorized users and services can access specific secrets.
Comprehensive Audit Logging: Detailed logs record who accessed specific secrets and when, providing essential data for security audits and incident response.
High Availability and Disaster Recovery: Secrets management solutions often offer high availability and disaster recovery features, ensuring business continuity.
Pros and Cons of Secrets Management
Let's take a quick look at the advantages and disadvantages:
| Pros | Cons |
|---|---|
| Removes secrets from code repositories | Introduces a dependency on the secrets service |
| Single source of truth for credentials | Potential added latency to application operation |
| Simplifies key rotation and revocation | Can be expensive for large enterprises |
| Detailed audit trails for compliance | Requires organizational buy-in and training |
Real-world examples demonstrate the value of secrets management. Companies using microservices architectures often use tools like HashiCorp Vault to dynamically issue short-lived credentials to individual services, minimizing the impact of potential breaches. Organizations working in cloud environments benefit from integrated solutions like AWS Secrets Manager or Azure Key Vault, streamlining secrets management within their cloud ecosystems. For DevOps environments, CyberArk Conjur offers robust secrets management tailored to automated workflows. For more information, check out our guide on API keys.
The growing adoption of DevSecOps and the influence of the Cloud Native Computing Foundation (CNCF) have further emphasized the importance of secrets management, highlighting the need for security throughout the software development lifecycle. HashiCorp's contributions, particularly with Vault, have significantly shaped the modern secrets management landscape.
Tips for Implementation
Caching: Implement client-side caching with appropriate TTLs (Time To Live) to minimize latency.
Emergency Access: Establish clear procedures for emergency access to secrets.
Infrastructure as Code (IaC): Use IaC to define and manage your secrets management configuration.
CI/CD Integration: Integrate with CI/CD pipelines to inject secrets during deployment, eliminating manual intervention.
Dynamic Secrets: Consider using dynamic secrets, generated on demand, to further reduce the impact of potential compromises.
This practice is essential because it directly mitigates a critical security vulnerability. By adopting a dedicated secrets management solution, organizations can significantly improve their security posture, simplify credential management, and build more robust and secure applications.
No spam, no nonsense. Pinky promise.
5. Comprehensive Monitoring and Anomaly Detection
API keys are essential for accessing your systems. Losing control of them can be a disaster. That’s why monitoring and anomaly detection are so important for any organization using APIs. It's a core best practice. This involves setting up systems that constantly track how API keys are used, analyze their behavior, and automatically find anything suspicious. This lets you react quickly to potential breaches before any serious damage is done.
This goes beyond simply recording API calls. It’s about understanding the bigger picture. Are the calls coming from the right places? Are the request volumes and frequencies typical? By establishing a baseline of normal behavior, you can effectively identify unusual activity that might suggest a compromised key or malicious intent.
Features of a Robust System
A robust monitoring and anomaly detection system should have several key features:
- Real-time Monitoring of API Key Usage: This gives you up-to-the-minute information on how your keys are being used.
- Behavioral Analysis: The system should learn the usual usage patterns for each key to form a baseline for anomaly detection.
- Anomaly Detection Algorithms: These algorithms identify unusual patterns, flagging potentially malicious activity.
- Integrated Alerting and Response: The system should automatically notify your security team about suspected problems, enabling a rapid response.
- Historical Usage Analytics: Detailed logs are essential for investigating past incidents and improving future detection.
Pros and Cons of Monitoring
Like any security measure, monitoring and anomaly detection come with both advantages and drawbacks.
Pros:
- Fast Detection of Compromised Credentials: This minimizes the time attackers have to exploit stolen keys.
- Visibility into API Key Usage: You gain valuable insights into API usage patterns and potential areas for improvement.
- Identification of Unused Keys: This helps streamline key management by identifying keys that can be revoked.
- Compliance Support: Monitoring supports compliance requirements for auditing and logging API access.
Cons:
- False Positives: The system might generate alerts for legitimate activity, requiring investigation.
- Ongoing Tuning: As usage patterns change, you'll need to adjust detection algorithms to maintain accuracy.
- Storage Requirements: Storing API logs long-term can use a lot of resources.
- Complex Implementation: Setting up and managing these systems across a large infrastructure can be challenging.
Real-World Examples and Practical Tips
Several tools offer API monitoring and anomaly detection:
- Datadog: Provides comprehensive API key usage monitoring and anomaly detection.
- AWS CloudTrail: Tracks API key usage across various AWS services.
- Splunk: Offers machine learning-based anomaly detection for API activity.
- Elastic Stack (ELK): Can be configured with custom anomaly detection rules for API monitoring.
Here are a few practical tips for implementing a monitoring system:
- Establish Clear Baselines: Understanding normal usage is crucial for accurate anomaly detection.
- Implement Rate Limiting: This restricts how many requests a key can make within a timeframe, limiting the damage from a compromised key.
- Automated Playbooks: Create automated responses for common key compromise scenarios.
- Alerting Thresholds: Set different alert levels based on how sensitive a key is.
- Regular Review: Regularly review and refine detection algorithms to stay ahead of evolving threats.
Evolution and Growing Importance
The increasing use of APIs and the rising threat of cyberattacks have made API key monitoring and anomaly detection more important than ever. Initiatives like Google's BeyondProd security model and the MITRE ATT&CK framework have further emphasized the need for continuous security monitoring and automated incident response. Netflix's advanced security practices have also influenced the wider adoption of these techniques, making strong API key security a top priority for organizations of all sizes.
6. Environmental Isolation and Context-Aware API Keys
API keys are essential for accessing your digital resources. Think of them like physical keys: you wouldn't use the same key for your house, car, and office. Similarly, using the same API key across different environments (development, testing, staging, and production) is risky. Environmental isolation, combined with context-aware restrictions, is a crucial best practice for API key management. This approach involves creating separate API keys for each environment, each with permissions tailored to its specific use case.
This compartmentalizes risk. A compromised key in a development environment won't impact your production data. Context-aware restrictions add layers of security. You can restrict access based on source IP, geographic location, or time of day. For example, configure an API key to accept requests only from your office's IP address range or prevent sensitive operations outside business hours.
Features of This Approach
- Environment-Specific API Keys: Assign appropriate permissions for each stage of development.
- Network-Based Restrictions: Control access using IP whitelisting and CIDR ranges.
- Geolocation-Based Access Controls: Limit access based on location.
- Time-of-Day Restrictions: Enhance security for sensitive operations.
- Application Identity Verification Requirements: Ensure only authorized applications use the API.
Pros and Cons
| Pros | Cons |
|---|---|
| Compartmentalized risk between environments | Increased number of keys to manage |
| Prevents credential leakage | Challenges for developers working across environments |
| Added security layers | Can complicate CI/CD pipelines and testing |
| Simplified key usage tracking | Requires infrastructure for context validation |
Real-world examples demonstrate this practice’s effectiveness. Stripe allows creating restricted API keys with IP address limitations. Twilio provides granular control over API key permissions. Cloudflare API tokens can be configured with specific hostnames and permissions. SendGrid enables restrictions by IP and permissions.
The importance of environmental isolation and context-aware API keys is reinforced by methodologies like the 12-Factor App, best practices from cloud providers like Google Cloud Platform, and platform-specific approaches like Heroku's environment-based configuration. These emphasize separating configuration from code and managing environment-specific settings.
Practical Implementation Tips
- Use distinct naming conventions (e.g.,
dev_api_key,prod_api_key). - Implement color coding in internal tools to differentiate environments.
- Create different security requirements based on environment sensitivity.
- Document procedures for moving applications between environments.
- Use infrastructure as code to manage configurations.
You might also be interested in: Our guide on Data Privacy Best Practices.
This practice is crucial for everyone working with APIs, from individual developers to large enterprises. It significantly boosts security by minimizing the impact of potential breaches and providing granular access control. By isolating environments and implementing context-aware restrictions, you strengthen your API security and protect your data.
7. API Key Transport Security Controls
Protecting your API keys isn't just about where you store them; it's also about how you transmit them. API Key Transport Security Controls focus on securing the journey of your API keys between systems, minimizing the risk of interception or accidental exposure. A leaked key in transit can be just as damaging as a compromised database.
The core principle is to treat API keys like the valuable secrets they are. This means applying robust security measures during their transmission. This goes beyond basic HTTPS and involves implementing standardized practices for key inclusion, utilizing stronger authentication mechanisms, and ensuring keys are never exposed in logs or other vulnerable locations.
Why This Matters: Imagine your API key embedded in a URL, visible in server logs, browser history, and network traffic. This is a security nightmare. Strong transport security prevents such scenarios, adding a critical layer of defense.
Features and Benefits of Secure API Key Transport
Standardized Header Usage: API keys should always be sent in HTTP headers (e.g.,
Authorizationheader), never as part of the URL. This prevents the key from appearing in server logs or browser history.TLS/HTTPS Enforcement: All API traffic should be encrypted using TLS/HTTPS. This is a fundamental requirement for secure communication, protecting data in transit from eavesdropping.
Mutual TLS (mTLS): For service-to-service communication, mTLS offers enhanced security by requiring both the client and the server to present valid certificates. This provides strong authentication and helps prevent man-in-the-middle attacks.
Token Exchange Patterns: In highly sensitive environments, consider using token exchange patterns like OAuth 2.0. This allows applications to access resources on behalf of a user without sharing the user's credentials.
Automatic Redaction in Logging Systems: Ensure your logging systems automatically redact or mask API keys and other sensitive information. This prevents accidental exposure.
Pros and Cons of Secure Transport
Let's summarize the advantages and disadvantages:
| Pros | Cons |
|---|---|
| Prevents key exposure in logs and URLs | Increased implementation complexity |
| Adds another layer of verification | May require additional infrastructure |
| Reduces man-in-the-middle attack risks | Potential compatibility issues with older systems |
| Creates defense-in-depth for authentication | Requires developer training and enforcement |
Real-World Examples of Secure Key Transport
Several major companies employ these security measures:
Google Cloud's HMAC Signing: Google uses HMAC (Hash-based Message Authentication Code) for signing API requests, providing integrity and authentication.
Netflix's Edge Authentication with mTLS: Netflix uses mTLS for authenticating services at the edge of their network, securing communication between internal services.
Amazon's Signature Version 4: AWS uses a sophisticated signing process involving cryptographic hashes and other parameters to authenticate API requests.
Kubernetes Webhook Token Authenticators: Kubernetes utilizes webhooks and token-based authentication for secure communication between components.
Practical Tips for Implementation
Here are a few practical steps you can take:
Use Headers: Always use headers (e.g.,
Authorization: Bearer <your_api_key>) for API keys, never URL parameters.Enforce HTTPS: Implement HTTP security headers like
Strict-Transport-Securityto enforce HTTPS.Utilize OAuth 2.0: Use standardized OAuth 2.0 flows when appropriate.
Consider JWTs: Consider JWT (JSON Web Tokens) with short expiration times for session-based access.
Redact Logs: Implement automatic logging redaction for
Authorizationand other sensitive headers.
Evolution and Popularity
The increasing reliance on APIs and growing awareness of security vulnerabilities have led to widespread adoption of these practices. Organizations like OWASP and major cloud providers like Google and AWS have helped standardize secure API key transport mechanisms. Their guidelines and best practices have significantly influenced the development community.
By implementing strong API Key Transport Security Controls, you add a crucial layer of protection to your APIs, minimizing the risk of key compromise and unauthorized access. This is essential for protecting your applications and data.
8. Developer Education and Secure API Key Handling Guidelines
API keys are essentially digital passwords granting access to your application's valuable data and functionalities. Misplaced keys can lead to serious consequences, including data breaches, service disruptions, and financial losses. That's why developer education and secure API key handling guidelines are essential for any API security strategy. This proactive approach empowers developers to manage API keys responsibly, reducing the risk of exposure and promoting a security-conscious development culture.
With the increasing use of APIs and the rise in security incidents due to compromised keys, secure key handling has become a top priority. Organizations like OWASP, Google Cloud, and Auth0 offer valuable resources and promote secure coding practices. The shift from simply distributing keys to implementing comprehensive training and tools reflects the understanding that human error is a major factor in API security breaches.
Key Features of a Robust API Key Handling Program
Documented Company Standards: Clear, easy-to-find documentation that outlines the rules and procedures for generating, storing, using, and rotating API keys.
Secure Code Examples and Templates: Providing developers with ready-made, secure code examples for typical API authentication situations prevents them from creating potentially vulnerable code from scratch.
Developer Training Programs: Dedicated training sessions and workshops that focus on API security best practices, ensuring developers understand the risks and how to address them.
Pre-commit Hooks and Code Scanning: Automated tools that can identify and prevent accidental commits of API keys to version control systems, catching errors before they pose a security threat. Tools like GitHub's secret scanning API and GitGuardian are invaluable for this.
Clear Incident Response Procedures: A well-defined process for handling exposed API keys, allowing for a rapid and effective response to minimize potential damage.
Pros of a Robust API Key Handling Program
- Proactive Prevention: Stops common security errors before they occur.
- Culture of Security: Fosters a security-minded development environment.
- Standardization: Creates consistent API key handling practices across different development teams.
- Cost Reduction: Lowers the costs associated with responding to exposed credentials.
Cons of a Robust API Key Handling Program
- Ongoing Investment: Requires continued investment in training and security tools.
- Initial Slowdown: Might initially slow down development while teams adapt to new procedures.
- Regular Updates: Needs frequent updates as security best practices and threats change.
- Enforcement Challenges: Can be difficult to enforce across large, geographically dispersed teams.
Practical Tips for Implementation
- Dedicated Documentation: Create a specific section in your developer documentation dedicated to API security.
- Pre-commit Hooks: Use pre-commit hooks to stop accidental key commits.
- Secure Code Snippets: Provide ready-to-use secure code examples for API authentication.
- Regular Training: Offer consistent security training with real-world examples and case studies.
- Automated Tools: Utilize automated tools such as GitHub's secret scanning and GitGuardian for potential key exposures.
- Key Rotation Procedures: Establish clear procedures for key rotation after suspected or confirmed exposure. AWS's IAM Key Last Used feature can be helpful here.
Real-World Examples
- Stripe: Offers comprehensive documentation on API key security best practices. (Check Stripe's developer documentation for specifics.)
- AWS: Provides the IAM Key Last Used feature for easier credential management and rotation. (Check AWS IAM documentation for specifics.)
Investing in developer education and clear API key handling guidelines significantly reduces API-related security risks, safeguards sensitive data, and creates a more secure application ecosystem. While this requires ongoing effort, it ultimately saves money by preventing costly security incidents and establishes a security-first mindset among development teams.
8-Point API Key Management Comparison
| Best Practice | Implementation Complexity 🔄 | Resource Requirements ⚡ | Expected Outcomes 📊 | Ideal Use Cases ⭐ | Tips 💡 |
|---|---|---|---|---|---|
| Encryption of API Keys at Rest and in Transit | Moderate – adds encryption and key management overhead | Moderate – requires strong encryption algorithms and monitoring | Enhances data confidentiality and mitigates breach risks | Regulated industries, cloud environments | Use envelope encryption; perform regular audits |
| Principle of Least Privilege for API Keys | Moderate to High – needs granular permission setups | Moderate – increased admin overhead and multi-key management | Reduces attack surface and simplifies audit trails | Multi-role environments, compliance-focused systems | Regularly audit permissions; separate read/write access |
| Automated Key Rotation and Expiration | High – demands robust automation and monitoring | High – requires automation tools and alerting infrastructure | Limits exposure window; enforces periodic security reviews | Dynamic key usage environments; sensitive operations | Overlap validity periods; set up expiration alerts |
| Secure Storage in Dedicated Secrets Management Solutions | Moderate to High – integration with specialized tools | Moderate – investment in secrets management platforms and training | Centralizes credential management with audit trails | Enterprise applications; DevOps environments | Use client-side caching; integrate with CI/CD pipelines |
| Comprehensive Monitoring and Anomaly Detection | High – complex tuning and continuous analysis required | High – advanced monitoring tools and extensive data storage | Enables rapid detection and effective incident response | Large-scale systems; high-security environments | Establish clear usage baselines; automate alerting mechanisms |
| Environmental Isolation and Context-Aware API Keys | Moderate – requires environment-specific configurations | Moderate – additional management of multiple keys and context validation | Compartmentalizes risk; prevents cross-environment misuse | Multi-environment development pipelines | Use distinct naming conventions and color coding; document processes |
| API Key Transport Security Controls | High – enforces strict protocol and mTLS requirements | High – needs modern infrastructure and secure transmission tools | Prevents interception and accidental logging of credentials | Systems with inter-service authentication and sensitive data | Always pass keys in headers; enforce TLS; use token exchange patterns |
| Developer Education and Secure API Key Handling Guidelines | Low to Moderate – depends on training program scope | Moderate – ongoing investment in tooling and security training | Fosters secure coding practices and reduces accidental exposures | Organizations with large or evolving development teams | Implement pre-commit hooks; update training and documentation regularly |
Level Up Your API Security
Managing API keys effectively is crucial for a secure and reliable application. Let's recap the key principles and how you can apply them to strengthen your API security. We've covered essential practices like encrypting API keys, both at rest and in transit. We also discussed adhering to the principle of least privilege.
This involves granting only the necessary permissions to each API key. We also touched on implementing automated key rotation and expiration. And let's not forget the importance of using secure storage solutions.
Robust monitoring and anomaly detection are your first line of defense against unauthorized access. Think of them as your security guards, constantly watching for suspicious activity.
Utilizing environmental isolation and context-aware API keys adds another layer of protection, limiting the impact of a compromised key. These measures help contain any potential damage. Finally, secure transport mechanisms and strong developer education are paramount.
By embracing these practices, you're not just protecting your data; you're building a culture of security. This involves educating your team on secure API key handling guidelines and staying informed about evolving threats. Knowledge is power, especially in the ever-changing world of security.
Key Takeaways
- Encryption is paramount: Protect your keys at all times, both in storage and during transmission.
- Least privilege is key: Grant only the necessary permissions to each API key.
- Rotate and expire: Regularly rotating keys minimizes the window of opportunity for attackers.
- Secure storage is essential: Use dedicated secrets management solutions, not configuration files.
- Monitor and detect anomalies: Proactive monitoring helps identify suspicious activity early.
- Context matters: Implement context-aware keys and environmental isolation for granular control.
- Secure transport is non-negotiable: Use HTTPS and other secure protocols.
- Education is your best defense: Train your team on secure API key handling practices.
The API landscape is constantly changing, with new threats and vulnerabilities emerging regularly. Stay ahead of the curve by keeping up with the latest trends in API security. This includes advancements in authentication methods, AI-powered threat detection, and blockchain-based security solutions.
Adapting to these changes and continuously refining your API key management strategy is essential for long-term success. By prioritizing API security, you protect your data, maintain user trust, and ensure the continued growth and stability of your applications.