Secure and Optimize Your API Key Azure Today
Learn proven tips to protect and manage your API Key Azure effectively. Enhance security and performance with expert strategies.
Decoding API Keys in the Azure Ecosystem

API keys in Azure act like digital keys, providing access to your valuable resources. These keys are essential for authenticating users and applications. Proper management of these keys is a core part of your cloud security strategy. It's not just about checking a box; it's about ensuring that only authorized users and apps can access your Azure services.
Understanding how API keys function is the first step towards a strong security posture.
API Key Azure vs. Other Authentication Methods
API keys offer a straightforward way to authenticate. However, they aren't always the best solution. Other methods, such as OAuth 2.0 and Managed Identities, offer more detailed control and stronger security.
OAuth 2.0, for example, is great for delegated access. It allows outside applications to access resources without directly handling sensitive credentials. Managed Identities, on the other hand, are perfectly suited for services running inside Azure. They remove the need for managing credentials altogether.
The best authentication method depends on your specific needs and the level of security you require.
Best Practices for Managing API Keys in Azure
Managing API keys effectively requires a balance between security and efficiency. This means understanding the entire lifecycle of your keys, from creation and storage to rotation and eventual revocation.
A key part of Azure API management involves the Azure Consumption APIs. These APIs provide programmatic access to cost and usage data for your Azure resources. They support a large portion of the Azure user base, including Enterprise Enrollments, Web Direct subscriptions, and CSP Azure plan subscriptions, with some exceptions. Learn more about Azure Consumption APIs.
The Azure Consumption APIs provide valuable information about your Azure spending and usage, including price sheets, budgets, and reservation details. This data is crucial for optimizing resource use and controlling costs. Using a centralized secrets management system, such as Azure Key Vault, can significantly bolster your security.
Real-World Applications of API Key Azure
Many organizations use API keys across a variety of Azure services. For instance, a company might use API keys to automate resource deployments using Azure Resource Manager (ARM) templates. Others might use them to control access to their Azure Functions or Azure Logic Apps.
When managed properly, API keys enable automation and secure access to a wide range of Azure services. This allows businesses to operate more efficiently and securely in the cloud. Understanding these applications can help you determine how best to use API keys within your own Azure environment.
Bulletproofing Your API Key Azure Credentials
Security breaches resulting from compromised API keys can have devastating consequences, yet they're entirely preventable. This section explores proven security strategies used by Azure experts who've managed sensitive authentication at scale. We'll cover how to safeguard your API keys throughout their lifecycle, from creation and storage to rotation and retirement.
Implementing Least Privilege Access
A fundamental security principle is implementing least privilege access. This means restricting API keys to only the permissions absolutely necessary for their intended function. This approach drastically reduces your attack surface by limiting the potential damage from a compromised key. For example, an API key used only for reading data shouldn't have write or delete permissions. This limits the impact of unauthorized access.
Secure Key Rotation and Encryption
Regular key rotation is crucial. Just like changing your passwords, rotating your API keys regularly minimizes the window of vulnerability. Combine this with strong encryption methods to protect your keys both in transit and at rest. Consider robust encryption algorithms like AES-256 to ensure data confidentiality. For more in-depth information, check out this guide: How to master API Key Management. It offers additional insights into API key security best practices.
Leveraging Azure Key Vault
Azure Key Vault provides a centralized and secure platform for managing your API keys. This service simplifies key rotation, access control, and encryption, significantly bolstering your security posture. The infographic below highlights the efficiency gains of automated key creation through CLI/ARM compared to manual creation, demonstrating both time saved and the reduction in error rate.
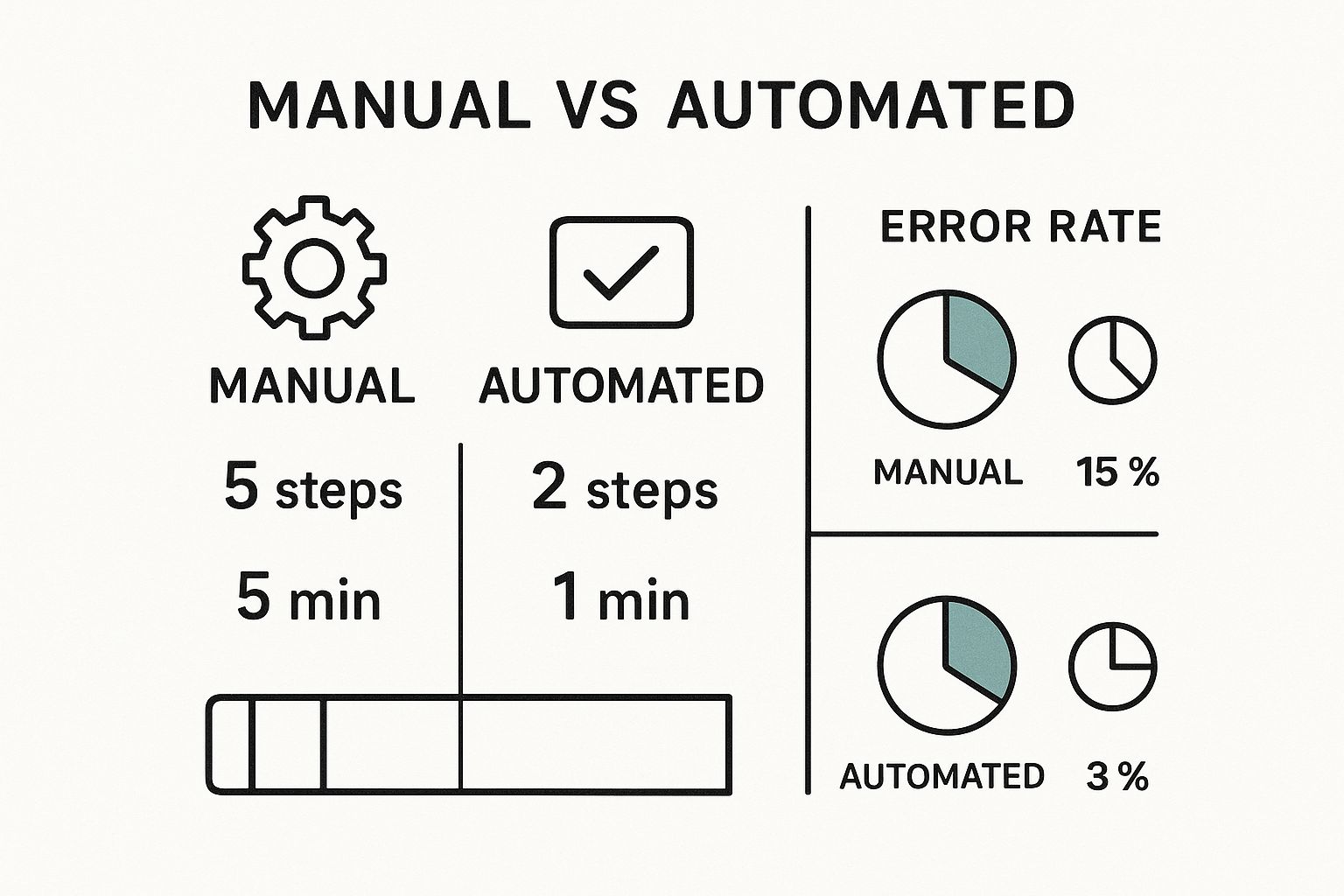
As shown, automated creation drastically reduces manual steps and time, leading to a much lower error rate. This efficiency boost is vital for maintaining strong security while minimizing operational overhead. Securing Azure Active Directory (AAD) API keys is critical due to potential exposure on platforms like GitHub. Tools like HashiCorp Vault and CyberArk Conjur are recommended for securely storing and managing Azure API keys. These tools provide secure environments for sensitive information, mitigating the risk of leaks. Swift key rotation and minimal service disruption are essential if leaks occur. This enhances infrastructure security and builds trust in cloud services. Learn more about securing Azure Active Directory API keys. When decoding API keys in Azure, understanding API management best practices is key. Check out this API Checklist GitHub resource.
Practical Examples and Best Practices
Imagine an application needing database access. Instead of embedding database credentials directly in the code, store them securely in Azure Key Vault. The application can then retrieve these credentials on demand, preventing exposure.
To recap, here are some best practices for securing your Azure API keys:
- Principle of Least Privilege: Grant only required permissions.
- Key Rotation: Schedule regular key rotations.
- Encryption: Encrypt keys both in transit and at rest.
- Centralized Management: Use Azure Key Vault.
- Secure Storage: Never embed keys directly in code.
Following these practices significantly enhances the security of your Azure API key infrastructure, protecting your valuable resources.
To further clarify the different approaches, let's compare several key security solutions:
Azure API Key Security Solutions Comparison
| Security Solution | Key Features | Integration Complexity | Cost Considerations | Best For |
|---|---|---|---|---|
| Azure Key Vault | Centralized key management, encryption, access control | Relatively simple integration with other Azure services | Pay-as-you-go pricing | Organizations using Azure services and needing robust key management |
| HashiCorp Vault | Secrets management, encryption, access control, multi-cloud support | Can be more complex to integrate, requires infrastructure setup | Open-source (free) and enterprise versions available | Organizations needing multi-cloud support or more advanced secrets management features |
| CyberArk Conjur | Secrets management, privileged access management, policy-based access control | Can be complex to integrate, requires infrastructure setup | Subscription-based pricing | Organizations with stringent security requirements and needing privileged access management |
This table highlights the key differences and similarities between these solutions, enabling you to choose the best fit for your specific needs. Each solution offers varying levels of complexity and cost, so consider your organization's requirements and resources. By carefully evaluating these factors, you can select the most effective solution for securing your Azure API keys.
Get started with your lifetime license
Enjoy unlimited conversations with MultitaskAI and unlock the full potential of cutting-edge language models—all with a one-time lifetime license.
Demo
Free
Try the full MultitaskAI experience with all features unlocked. Perfect for testing before you buy.
- Full feature access
- All AI model integrations
- Split-screen multitasking
- File uploads and parsing
- Custom agents and prompts
- Data is not saved between sessions
Lifetime License
Most Popular€99€149
One-time purchase for unlimited access, lifetime updates, and complete data control.
- Everything in Free
- Data persistence across sessions
- MultitaskAI Cloud sync
- Cross-device synchronization
- 5 device activations
- Lifetime updates
- Self-hosting option
- Priority support
Loved by users worldwide
See what our community says about their MultitaskAI experience.
Finally found a ChatGPT alternative that actually respects my privacy. The split-screen feature is a game changer for comparing models.
Sarah
Been using this for months now. The fact that I only pay for what I use through my own API keys saves me so much money compared to subscriptions.
Marcus
The offline support is incredible. I can work on my AI projects even when my internet is spotty. Pure genius.
Elena
Love how I can upload files and create custom agents. Makes my workflow so much more efficient than basic chat interfaces.
David
Self-hosting this was easier than I expected. Now I have complete control over my data and conversations.
Rachel
The background processing feature lets me work on multiple conversations at once. No more waiting around for responses.
Alex
Switched from ChatGPT Plus and haven't looked back. This gives me access to all the same models with way more features.
Maya
Finally found a ChatGPT alternative that actually respects my privacy. The split-screen feature is a game changer for comparing models.
Sarah
Been using this for months now. The fact that I only pay for what I use through my own API keys saves me so much money compared to subscriptions.
Marcus
The offline support is incredible. I can work on my AI projects even when my internet is spotty. Pure genius.
Elena
Love how I can upload files and create custom agents. Makes my workflow so much more efficient than basic chat interfaces.
David
Self-hosting this was easier than I expected. Now I have complete control over my data and conversations.
Rachel
The background processing feature lets me work on multiple conversations at once. No more waiting around for responses.
Alex
Switched from ChatGPT Plus and haven't looked back. This gives me access to all the same models with way more features.
Maya
Finally found a ChatGPT alternative that actually respects my privacy. The split-screen feature is a game changer for comparing models.
Sarah
Been using this for months now. The fact that I only pay for what I use through my own API keys saves me so much money compared to subscriptions.
Marcus
The offline support is incredible. I can work on my AI projects even when my internet is spotty. Pure genius.
Elena
Love how I can upload files and create custom agents. Makes my workflow so much more efficient than basic chat interfaces.
David
Self-hosting this was easier than I expected. Now I have complete control over my data and conversations.
Rachel
The background processing feature lets me work on multiple conversations at once. No more waiting around for responses.
Alex
Switched from ChatGPT Plus and haven't looked back. This gives me access to all the same models with way more features.
Maya
Finally found a ChatGPT alternative that actually respects my privacy. The split-screen feature is a game changer for comparing models.
Sarah
Been using this for months now. The fact that I only pay for what I use through my own API keys saves me so much money compared to subscriptions.
Marcus
The offline support is incredible. I can work on my AI projects even when my internet is spotty. Pure genius.
Elena
Love how I can upload files and create custom agents. Makes my workflow so much more efficient than basic chat interfaces.
David
Self-hosting this was easier than I expected. Now I have complete control over my data and conversations.
Rachel
The background processing feature lets me work on multiple conversations at once. No more waiting around for responses.
Alex
Switched from ChatGPT Plus and haven't looked back. This gives me access to all the same models with way more features.
Maya
Switched from ChatGPT Plus and haven't looked back. This gives me access to all the same models with way more features.
Maya
The sync across devices works flawlessly. I can start a conversation on my laptop and continue on my phone seamlessly.
James
As a developer, having all my chats, files, and agents organized in one place has transformed how I work with AI.
Sofia
The lifetime license was such a smart purchase. No more monthly fees, just pure productivity.
Ryan
Queue requests feature is brilliant. I can line up my questions and let the AI work through them while I focus on other tasks.
Lisa
Having access to Claude, GPT-4, and Gemini all in one interface is exactly what I needed for my research.
Mohamed
The file parsing capabilities saved me hours of work. Just drag and drop documents and the AI understands everything.
Emma
Switched from ChatGPT Plus and haven't looked back. This gives me access to all the same models with way more features.
Maya
The sync across devices works flawlessly. I can start a conversation on my laptop and continue on my phone seamlessly.
James
As a developer, having all my chats, files, and agents organized in one place has transformed how I work with AI.
Sofia
The lifetime license was such a smart purchase. No more monthly fees, just pure productivity.
Ryan
Queue requests feature is brilliant. I can line up my questions and let the AI work through them while I focus on other tasks.
Lisa
Having access to Claude, GPT-4, and Gemini all in one interface is exactly what I needed for my research.
Mohamed
The file parsing capabilities saved me hours of work. Just drag and drop documents and the AI understands everything.
Emma
Switched from ChatGPT Plus and haven't looked back. This gives me access to all the same models with way more features.
Maya
The sync across devices works flawlessly. I can start a conversation on my laptop and continue on my phone seamlessly.
James
As a developer, having all my chats, files, and agents organized in one place has transformed how I work with AI.
Sofia
The lifetime license was such a smart purchase. No more monthly fees, just pure productivity.
Ryan
Queue requests feature is brilliant. I can line up my questions and let the AI work through them while I focus on other tasks.
Lisa
Having access to Claude, GPT-4, and Gemini all in one interface is exactly what I needed for my research.
Mohamed
The file parsing capabilities saved me hours of work. Just drag and drop documents and the AI understands everything.
Emma
Switched from ChatGPT Plus and haven't looked back. This gives me access to all the same models with way more features.
Maya
The sync across devices works flawlessly. I can start a conversation on my laptop and continue on my phone seamlessly.
James
As a developer, having all my chats, files, and agents organized in one place has transformed how I work with AI.
Sofia
The lifetime license was such a smart purchase. No more monthly fees, just pure productivity.
Ryan
Queue requests feature is brilliant. I can line up my questions and let the AI work through them while I focus on other tasks.
Lisa
Having access to Claude, GPT-4, and Gemini all in one interface is exactly what I needed for my research.
Mohamed
The file parsing capabilities saved me hours of work. Just drag and drop documents and the AI understands everything.
Emma
The file parsing capabilities saved me hours of work. Just drag and drop documents and the AI understands everything.
Emma
Dark mode, keyboard shortcuts, and the clean interface make this a joy to use daily.
Carlos
Fork conversations feature is perfect for exploring different ideas without losing my original train of thought.
Aisha
The custom agents with specific instructions have made my content creation process so much more streamlined.
Thomas
Best investment I've made for my AI workflow. The features here put other chat interfaces to shame.
Zoe
Privacy-first approach was exactly what I was looking for. My data stays mine.
Igor
The PWA works perfectly on mobile. I can access all my conversations even when I'm offline.
Priya
Support team is amazing. Quick responses and they actually listen to user feedback for improvements.
Nathan
The file parsing capabilities saved me hours of work. Just drag and drop documents and the AI understands everything.
Emma
Dark mode, keyboard shortcuts, and the clean interface make this a joy to use daily.
Carlos
Fork conversations feature is perfect for exploring different ideas without losing my original train of thought.
Aisha
The custom agents with specific instructions have made my content creation process so much more streamlined.
Thomas
Best investment I've made for my AI workflow. The features here put other chat interfaces to shame.
Zoe
Privacy-first approach was exactly what I was looking for. My data stays mine.
Igor
The PWA works perfectly on mobile. I can access all my conversations even when I'm offline.
Priya
Support team is amazing. Quick responses and they actually listen to user feedback for improvements.
Nathan
The file parsing capabilities saved me hours of work. Just drag and drop documents and the AI understands everything.
Emma
Dark mode, keyboard shortcuts, and the clean interface make this a joy to use daily.
Carlos
Fork conversations feature is perfect for exploring different ideas without losing my original train of thought.
Aisha
The custom agents with specific instructions have made my content creation process so much more streamlined.
Thomas
Best investment I've made for my AI workflow. The features here put other chat interfaces to shame.
Zoe
Privacy-first approach was exactly what I was looking for. My data stays mine.
Igor
The PWA works perfectly on mobile. I can access all my conversations even when I'm offline.
Priya
Support team is amazing. Quick responses and they actually listen to user feedback for improvements.
Nathan
The file parsing capabilities saved me hours of work. Just drag and drop documents and the AI understands everything.
Emma
Dark mode, keyboard shortcuts, and the clean interface make this a joy to use daily.
Carlos
Fork conversations feature is perfect for exploring different ideas without losing my original train of thought.
Aisha
The custom agents with specific instructions have made my content creation process so much more streamlined.
Thomas
Best investment I've made for my AI workflow. The features here put other chat interfaces to shame.
Zoe
Privacy-first approach was exactly what I was looking for. My data stays mine.
Igor
The PWA works perfectly on mobile. I can access all my conversations even when I'm offline.
Priya
Support team is amazing. Quick responses and they actually listen to user feedback for improvements.
Nathan
Mastering API Key Creation in the Azure Portal
Successfully managing API keys is crucial for anyone working with the Azure Portal. This guide offers practical advice on creating API keys for various Azure services. We'll also cover best practices for configuration, naming, documentation, and governance.
Creating an API Key in Azure: A Step-by-Step Guide
Creating an API key in Azure might vary slightly depending on the service you're using. However, the general process is fairly consistent. First, find the service you need in the Azure portal. Then, look for the "Keys" or "Authentication" section in that service's settings.
- Click the "Add" or "Generate key" button.
- Give your key a descriptive name. This helps you easily identify its purpose later on.
- Choose the specific access permissions or scope for the key. Remember the principle of least privilege: grant only the access that's absolutely necessary.
- After the key is generated, store it securely. Azure Key Vault is a great tool for this.
Keep in mind that the full key might not be shown again after you leave this screen. This is a security measure, so it’s essential to store your key safely from the start.
Best Practices for API Key Naming and Documentation
As the number of API keys you manage increases, using clear and consistent naming conventions becomes vital. A well-defined structure makes it simple to identify the purpose of a key and the service it belongs to. For instance, you could use a prefix that indicates both the service and the environment, followed by a descriptive name.
Documentation is equally important. Be sure to document the key's purpose, creation date, the service it's associated with, and any access restrictions. Good documentation prevents issues and simplifies troubleshooting, saving you time and effort. For further reading on API authentication methods, check out this helpful guide: How to master different API authentication methods.
Streamlining API Key Governance
Robust governance workflows are essential for managing API keys, especially as your organization grows. This involves establishing clear processes for creation, rotation, and revocation. Regularly rotating your keys, ideally on an automated schedule, minimizes the impact of potential security breaches.
Clearly defined roles and responsibilities are also part of good governance. This clarifies who has access to which keys, ensuring a more secure environment. For example, assign specific teams the responsibility for rotating keys for certain services. This promotes accountability and prevents unauthorized access.
Addressing Challenges of Scale
Managing a large volume of API keys can be complex. Centralized management platforms, such as Azure Key Vault, simplify this process and improve security. These platforms provide features like automated rotation, access control, and auditing.
Automated key rotation policies are a crucial feature of these platforms. They reduce the risk of using old, potentially compromised keys. This streamlined approach to API key governance is especially important for larger organizations. Proactive key management reduces vulnerabilities and strengthens your overall security posture.
Transforming API Key Data into Strategic Insights
Effective API key management within Azure involves more than just creation and storage. It's about using the data generated by API usage to gain valuable insights into your applications and services. This data can be instrumental in improving performance, optimizing costs, and bolstering security. Organizations that prioritize this data analysis are gaining a competitive advantage.
Building Monitoring Dashboards for Real-Time Visibility
One of the best ways to use API key data is by creating monitoring dashboards. These dashboards provide a real-time overview of your API ecosystem, allowing you to quickly identify potential problems like performance bottlenecks or unusual usage patterns. For example, a sudden surge in API calls from an unknown location could signal a security breach.
Visualizing key metrics, such as request latency, error rates, and usage volume, gives you a clear picture of API performance. This real-time visibility allows for proactive intervention, preventing small issues from becoming major incidents. These dashboards also offer valuable historical data for trend analysis and resource optimization.
Setting Up Intelligent Alerting Systems
Intelligent alerting systems enhance the proactive management provided by monitoring dashboards. These systems go beyond basic threshold-based alerts. They use machine learning to differentiate between normal fluctuations and actual anomalies. This reduces alert fatigue, so your team can focus on real threats.
An intelligent alerting system can learn the typical usage patterns for your API key during different times of the day. This allows it to filter out expected traffic spikes and alert you only to truly unusual behavior. This targeted approach improves response times and enhances your overall security.
Analyzing Consumption Metrics for Cost Optimization and Rate Limiting
API key usage data provides valuable insights for cost optimization. Analyzing consumption metrics helps you pinpoint areas of high usage and explore ways to reduce unnecessary API calls. This data also informs effective rate limiting strategies, which prevent abuse and ensure equitable access for all users. Azure offers detailed logging and metrics for API calls, enabling precise tracking of usage and the identification of potential cost savings.
To support this analysis, let's look at the monitoring capabilities across several Azure services. The table below summarizes the key features available for tracking API key usage and gaining insights.
Azure Services API Key Monitoring Capabilities:
| Azure Service | Monitoring Metrics Available | Alert Capabilities | Usage Visualization | Retention Period |
|---|---|---|---|---|
| Azure API Management | Request count, bandwidth, latency, errors | Threshold-based alerts, integration with Azure Monitor | Charts and dashboards within the Azure portal | Configurable, up to 90 days |
| Azure Functions | Executions, duration, errors, throttles | Metrics-based alerts through Azure Monitor | Azure portal dashboards and integration with other monitoring tools | Configurable, up to 90 days |
| Azure Logic Apps | Runs, actions, trigger history, failures | Alerts based on run status and failures | Azure portal visualizations and logs | Variable, depending on the pricing tier |
| Azure Kubernetes Service (AKS) | Resource usage, pod health, container metrics | Integration with Kubernetes monitoring tools and Azure Monitor | Dashboards and custom visualizations | Depends on chosen monitoring solution |
This table highlights the different monitoring metrics available for various Azure services, emphasizing the importance of leveraging these tools for comprehensive API key management. Understanding these metrics empowers you to make informed decisions about cost optimization, performance tuning, and security enhancements.
It's also important to consider the usage metrics provided by specific Azure services. Azure Maps, for example, offers detailed usage insights. As of April 2025, Azure Maps API usage can be monitored through the Azure portal. This gives developers a clear understanding of how their mapping services are used within applications. Learn more about Azure Maps API usage. This visibility is vital for optimizing costs and application performance, especially for businesses using location-based services.
By combining real-time monitoring, intelligent alerting, and in-depth consumption analysis, you can transform your API key data into actionable intelligence. These insights empower data-driven decisions, enhance application performance, and ultimately achieve a more secure and cost-effective API strategy.
Building Resilient API Key Authentication Systems
Building a robust and secure API key authentication system is critical for protecting your Azure resources. This goes beyond simply creating keys and involves understanding practical implementation strategies that can handle real-world security challenges. It's about connecting theory with practice through functional code examples and exploring more advanced authentication patterns. You might be interested in: How to master API Key Security Best Practices.
Implementing Best Practices With Code Examples
Protecting your API keys requires a multi-layered approach. Secure storage is a fundamental aspect of this. Never embed API keys directly in your application code. Instead, use secure storage solutions like Azure Key Vault.
For example, in Python, you can use the azure-keyvault-secrets library to retrieve your API key from Key Vault:
from azure.keyvault.secrets import SecretClient from azure.identity import DefaultAzureCredential
credential = DefaultAzureCredential() client = SecretClient(vault_url="your_key_vault_url", credential=credential)
retrieved_secret = client.get_secret("your_api_key_name") api_key = retrieved_secret.value
This keeps your API key separate from your codebase, greatly reducing the risk of accidental exposure.
In addition to secure storage, implement retry logic. If your API key is rotated, your application needs to handle temporary failures gracefully and retry the request using the new key. This ensures service availability during key rotations and a smooth user experience.
Advanced Authentication Patterns for Azure Applications
Basic API key authentication works for some scenarios, but high-performing Azure applications often require more sophisticated patterns. One option is to combine API keys with IP address restrictions. This adds another security layer by only permitting requests from approved IP addresses.
Another effective strategy is using API keys with OAuth 2.0. This is particularly useful when granting third-party applications access to your resources without sharing your actual API key. OAuth 2.0 provides a more secure and controlled method for delegating access.
Specialized Considerations for Different Architectures
The optimal API key authentication approach depends on your application's architecture. For microservices architectures, each microservice might have its own dedicated API key, adhering to the principle of least privilege.
For multi-tenant applications, scope API keys to individual tenants. This ensures that tenants only access their own data, improving data isolation and security. In serverless functions, such as Azure Functions, utilize managed identities whenever possible. This removes the need to manage API keys directly, providing a more secure and efficient authentication process. These targeted strategies significantly strengthen your overall API security in Azure, protecting your valuable resources and ensuring continuous service availability.
No spam, no nonsense. Pinky promise.
Resolving Common API Key Azure Challenges
Even the most well-designed API key systems can encounter issues. This section provides troubleshooting tools for problems with your API key Azure integration. We'll explore how to diagnose and resolve common API key issues, from understanding error messages to implementing preventative measures.
Decoding Cryptic Error Messages
One of the first signs of trouble is often a cryptic error message. Understanding these messages is crucial. A 401 Unauthorized error commonly indicates an invalid or expired API key. A 403 Forbidden error, however, suggests a permissions issue, even with a valid key. Comprehensive logging is essential for effective troubleshooting.
Log the timestamp, the API key used (partially masked for security), the specific request made, and the complete error response. This detailed information helps pinpoint the root cause faster, especially in complex systems with multiple interacting services.
Implementing Comprehensive Logging Strategies
Thorough logging accelerates problem resolution. Logging key details like timestamps, the partially masked API key used, the request made, and the full error response provides a valuable trail for debugging. Tools like Azure Monitor can further enhance your logging and diagnostic capabilities. For more on Azure authentication, see this resource: Auth.
Leveraging Azure-Specific Diagnostic Tools
Azure offers powerful diagnostic tools to pinpoint authentication failures. Azure Monitor provides deep insights into API calls, resource usage, and performance bottlenecks. You can configure alerts for specific error codes or unusual activity.
Azure Network Watcher can analyze network traffic related to your API calls, helping isolate network connectivity issues. Using these tools can drastically reduce troubleshooting time.
Case Studies: Real-World API Key Azure Problem Solving
Let's explore some common API key challenges and their solutions:
Scenario: An application suddenly receives 403 Forbidden errors when accessing an Azure resource.
- Solution: Review the API key's permissions in the Azure portal. Verify the key has the necessary access rights. If the key has expired or been revoked, generate a new one.
Scenario: An application experiences intermittent 503 Service Unavailable errors.
- Solution: This might indicate rate limiting. Check the service's documentation for rate limits and consider implementing retry logic with exponential backoff. This helps your application handle temporary service interruptions.
Scenario: Difficulty tracking the source of API calls due to shared keys.
- Solution: Implement unique API keys for each application or user. This simplifies tracking and allows fine-grained control over access.
Engaging Azure Support
Knowing when to engage Azure support is essential. Contact support for complex issues involving potential platform-level problems. When contacting support, provide detailed information: error messages, timestamps, affected services, and troubleshooting steps already taken. Clear communication ensures a quicker resolution.
By combining proactive logging, using Azure's diagnostic tools, and understanding common resolution paths, you can effectively address API key challenges, ensuring secure and reliable operation of your Azure applications.