Best API Authentication Methods for Secure Data
Secure your APIs with leading api authentication methods. Discover strategies like API Keys, OAuth 2.0, and JWT to protect your data.
Protecting Your Data: Choosing the Right API Authentication Method
APIs are everywhere, and securing them is critical. This listicle covers seven popular API authentication methods—API Keys, OAuth 2.0, JSON Web Tokens (JWT), Basic Authentication, OpenID Connect (OIDC), HMAC Authentication, and Mutual TLS (mTLS)—to help you choose the best way to protect your data. We'll explore each method's strengths and weaknesses so you can make informed security decisions for your applications, whether public-facing or internal. Let's get started.
1. API Keys
API keys are a fundamental method for authenticating requests to an API. Think of them as simple passwords for your application. Each key is a unique string of characters assigned to a specific user or application, acting as an identifier when making API calls. These keys are typically sent along with the request, either in the header (e.g., x-api-key) or as a query parameter (e.g., ?api_key=YOUR_API_KEY). This allows the API server to verify the caller's identity and grant access to the requested resources. API keys provide a straightforward way to manage access without the complexity of more advanced authentication mechanisms.
API keys are valued for their simplicity and ease of implementation. They are string-based, stateless (meaning the server doesn't need to store session information), and require no encryption or signature calculation. This makes them quick to integrate for both the client making the request and the server handling it. Moreover, API keys can be easily rotated or revoked, providing a simple way to manage security and control access. Learn more about API Keys to delve deeper into best practices for managing and securing them.
Features:
- Simple string-based identification
- Stateless implementation
- No encryption or signature required
- Easy to implement and use
- Can be rotated or revoked as needed
Pros:
- Very simple to implement for both client and server
- Low overhead and high performance
- Good for public APIs with limited access requirements
- Easy to rotate in case of suspected breach
- Ideal for internal or partner-facing APIs
Cons:
- Limited security as they're typically sent in plaintext
- Often vulnerable to interception in transit if not using HTTPS
- No built-in expiration mechanism
- Not suitable for controlling access to sensitive data
- No inherent user context - identifies the application, not the user
Examples:
- Google Cloud Platform: Uses API keys for accessing various cloud services.
- Stripe API: Employs API keys for payment processing integration.
- Mailchimp: Provides API keys for automating email marketing tasks.
- GitHub: Utilizes API keys for repository operations.
- Weather APIs: Services like OpenWeatherMap and AccuWeather use API keys for data access.
Tips for Secure API Key Management:
- Always use HTTPS: Encrypting communication between the client and server is crucial to protect API keys from interception.
- Implement rate limiting: This prevents abuse and denial-of-service attacks.
- Rotate keys regularly: Regular rotation minimizes the impact of a compromised key. Rotate keys immediately upon any suspected compromise.
- Use separate keys for different environments: Maintain separate keys for development, staging, and production environments to isolate potential security breaches.
- Secure storage: Store API keys securely, preferably using environment variables or dedicated secret management services. Never commit API keys to version control.
API keys earn their place on this list because they offer an excellent balance of simplicity and functionality for many API use cases. They're a perfect starting point for developers new to API authentication and are a practical choice for applications with less stringent security requirements, such as public APIs offering access to non-sensitive data. However, it's essential to be aware of their limitations and follow security best practices to mitigate risks.
Get started with your lifetime license
Enjoy unlimited conversations with MultitaskAI and unlock the full potential of cutting-edge language models—all with a one-time lifetime license.
Demo
Free
Try the full MultitaskAI experience with all features unlocked. Perfect for testing before you buy.
- Full feature access
- All AI model integrations
- Split-screen multitasking
- File uploads and parsing
- Custom agents and prompts
- Data is not saved between sessions
Lifetime License
Most Popular€99€149
One-time purchase for unlimited access, lifetime updates, and complete data control.
- Everything in Free
- Data persistence across sessions
- MultitaskAI Cloud sync
- Cross-device synchronization
- 5 device activations
- Lifetime updates
- Self-hosting option
- Priority support
Loved by users worldwide
See what our community says about their MultitaskAI experience.
Finally found a ChatGPT alternative that actually respects my privacy. The split-screen feature is a game changer for comparing models.
Sarah
Been using this for months now. The fact that I only pay for what I use through my own API keys saves me so much money compared to subscriptions.
Marcus
The offline support is incredible. I can work on my AI projects even when my internet is spotty. Pure genius.
Elena
Love how I can upload files and create custom agents. Makes my workflow so much more efficient than basic chat interfaces.
David
Self-hosting this was easier than I expected. Now I have complete control over my data and conversations.
Rachel
The background processing feature lets me work on multiple conversations at once. No more waiting around for responses.
Alex
Switched from ChatGPT Plus and haven't looked back. This gives me access to all the same models with way more features.
Maya
Finally found a ChatGPT alternative that actually respects my privacy. The split-screen feature is a game changer for comparing models.
Sarah
Been using this for months now. The fact that I only pay for what I use through my own API keys saves me so much money compared to subscriptions.
Marcus
The offline support is incredible. I can work on my AI projects even when my internet is spotty. Pure genius.
Elena
Love how I can upload files and create custom agents. Makes my workflow so much more efficient than basic chat interfaces.
David
Self-hosting this was easier than I expected. Now I have complete control over my data and conversations.
Rachel
The background processing feature lets me work on multiple conversations at once. No more waiting around for responses.
Alex
Switched from ChatGPT Plus and haven't looked back. This gives me access to all the same models with way more features.
Maya
Finally found a ChatGPT alternative that actually respects my privacy. The split-screen feature is a game changer for comparing models.
Sarah
Been using this for months now. The fact that I only pay for what I use through my own API keys saves me so much money compared to subscriptions.
Marcus
The offline support is incredible. I can work on my AI projects even when my internet is spotty. Pure genius.
Elena
Love how I can upload files and create custom agents. Makes my workflow so much more efficient than basic chat interfaces.
David
Self-hosting this was easier than I expected. Now I have complete control over my data and conversations.
Rachel
The background processing feature lets me work on multiple conversations at once. No more waiting around for responses.
Alex
Switched from ChatGPT Plus and haven't looked back. This gives me access to all the same models with way more features.
Maya
Finally found a ChatGPT alternative that actually respects my privacy. The split-screen feature is a game changer for comparing models.
Sarah
Been using this for months now. The fact that I only pay for what I use through my own API keys saves me so much money compared to subscriptions.
Marcus
The offline support is incredible. I can work on my AI projects even when my internet is spotty. Pure genius.
Elena
Love how I can upload files and create custom agents. Makes my workflow so much more efficient than basic chat interfaces.
David
Self-hosting this was easier than I expected. Now I have complete control over my data and conversations.
Rachel
The background processing feature lets me work on multiple conversations at once. No more waiting around for responses.
Alex
Switched from ChatGPT Plus and haven't looked back. This gives me access to all the same models with way more features.
Maya
Switched from ChatGPT Plus and haven't looked back. This gives me access to all the same models with way more features.
Maya
The sync across devices works flawlessly. I can start a conversation on my laptop and continue on my phone seamlessly.
James
As a developer, having all my chats, files, and agents organized in one place has transformed how I work with AI.
Sofia
The lifetime license was such a smart purchase. No more monthly fees, just pure productivity.
Ryan
Queue requests feature is brilliant. I can line up my questions and let the AI work through them while I focus on other tasks.
Lisa
Having access to Claude, GPT-4, and Gemini all in one interface is exactly what I needed for my research.
Mohamed
The file parsing capabilities saved me hours of work. Just drag and drop documents and the AI understands everything.
Emma
Switched from ChatGPT Plus and haven't looked back. This gives me access to all the same models with way more features.
Maya
The sync across devices works flawlessly. I can start a conversation on my laptop and continue on my phone seamlessly.
James
As a developer, having all my chats, files, and agents organized in one place has transformed how I work with AI.
Sofia
The lifetime license was such a smart purchase. No more monthly fees, just pure productivity.
Ryan
Queue requests feature is brilliant. I can line up my questions and let the AI work through them while I focus on other tasks.
Lisa
Having access to Claude, GPT-4, and Gemini all in one interface is exactly what I needed for my research.
Mohamed
The file parsing capabilities saved me hours of work. Just drag and drop documents and the AI understands everything.
Emma
Switched from ChatGPT Plus and haven't looked back. This gives me access to all the same models with way more features.
Maya
The sync across devices works flawlessly. I can start a conversation on my laptop and continue on my phone seamlessly.
James
As a developer, having all my chats, files, and agents organized in one place has transformed how I work with AI.
Sofia
The lifetime license was such a smart purchase. No more monthly fees, just pure productivity.
Ryan
Queue requests feature is brilliant. I can line up my questions and let the AI work through them while I focus on other tasks.
Lisa
Having access to Claude, GPT-4, and Gemini all in one interface is exactly what I needed for my research.
Mohamed
The file parsing capabilities saved me hours of work. Just drag and drop documents and the AI understands everything.
Emma
Switched from ChatGPT Plus and haven't looked back. This gives me access to all the same models with way more features.
Maya
The sync across devices works flawlessly. I can start a conversation on my laptop and continue on my phone seamlessly.
James
As a developer, having all my chats, files, and agents organized in one place has transformed how I work with AI.
Sofia
The lifetime license was such a smart purchase. No more monthly fees, just pure productivity.
Ryan
Queue requests feature is brilliant. I can line up my questions and let the AI work through them while I focus on other tasks.
Lisa
Having access to Claude, GPT-4, and Gemini all in one interface is exactly what I needed for my research.
Mohamed
The file parsing capabilities saved me hours of work. Just drag and drop documents and the AI understands everything.
Emma
The file parsing capabilities saved me hours of work. Just drag and drop documents and the AI understands everything.
Emma
Dark mode, keyboard shortcuts, and the clean interface make this a joy to use daily.
Carlos
Fork conversations feature is perfect for exploring different ideas without losing my original train of thought.
Aisha
The custom agents with specific instructions have made my content creation process so much more streamlined.
Thomas
Best investment I've made for my AI workflow. The features here put other chat interfaces to shame.
Zoe
Privacy-first approach was exactly what I was looking for. My data stays mine.
Igor
The PWA works perfectly on mobile. I can access all my conversations even when I'm offline.
Priya
Support team is amazing. Quick responses and they actually listen to user feedback for improvements.
Nathan
The file parsing capabilities saved me hours of work. Just drag and drop documents and the AI understands everything.
Emma
Dark mode, keyboard shortcuts, and the clean interface make this a joy to use daily.
Carlos
Fork conversations feature is perfect for exploring different ideas without losing my original train of thought.
Aisha
The custom agents with specific instructions have made my content creation process so much more streamlined.
Thomas
Best investment I've made for my AI workflow. The features here put other chat interfaces to shame.
Zoe
Privacy-first approach was exactly what I was looking for. My data stays mine.
Igor
The PWA works perfectly on mobile. I can access all my conversations even when I'm offline.
Priya
Support team is amazing. Quick responses and they actually listen to user feedback for improvements.
Nathan
The file parsing capabilities saved me hours of work. Just drag and drop documents and the AI understands everything.
Emma
Dark mode, keyboard shortcuts, and the clean interface make this a joy to use daily.
Carlos
Fork conversations feature is perfect for exploring different ideas without losing my original train of thought.
Aisha
The custom agents with specific instructions have made my content creation process so much more streamlined.
Thomas
Best investment I've made for my AI workflow. The features here put other chat interfaces to shame.
Zoe
Privacy-first approach was exactly what I was looking for. My data stays mine.
Igor
The PWA works perfectly on mobile. I can access all my conversations even when I'm offline.
Priya
Support team is amazing. Quick responses and they actually listen to user feedback for improvements.
Nathan
The file parsing capabilities saved me hours of work. Just drag and drop documents and the AI understands everything.
Emma
Dark mode, keyboard shortcuts, and the clean interface make this a joy to use daily.
Carlos
Fork conversations feature is perfect for exploring different ideas without losing my original train of thought.
Aisha
The custom agents with specific instructions have made my content creation process so much more streamlined.
Thomas
Best investment I've made for my AI workflow. The features here put other chat interfaces to shame.
Zoe
Privacy-first approach was exactly what I was looking for. My data stays mine.
Igor
The PWA works perfectly on mobile. I can access all my conversations even when I'm offline.
Priya
Support team is amazing. Quick responses and they actually listen to user feedback for improvements.
Nathan
2. OAuth 2.0
OAuth 2.0 is the industry-standard authorization framework for granting third-party applications limited access to user data on an HTTP service without sharing their passwords. Instead of directly accessing usernames and passwords, OAuth 2.0 allows applications to obtain an access token that represents the user's authorization to access specific resources. This delegation of authentication to the service provider (like Google, Facebook, or Twitter) and subsequent authorization of third-party apps enhances security and user control. OAuth 2.0 operates by separating authentication from authorization, enabling fine-grained control over what data an application can access.
OAuth 2.0's versatility comes from its support for various grant types, catering to different application architectures and security requirements. These grant types define how an application obtains an access token. For instance, the Authorization Code grant is commonly used for web applications, while the Client Credentials grant is suitable for server-to-server communication. This flexibility, combined with its token-based approach, allows developers to integrate a wide range of services securely and efficiently. If you're building an API integration, you can learn more about OAuth 2.0 to delve deeper into its implementation.
OAuth 2.0 deserves its place on this list due to its widespread adoption and robust security features. It offers a balance between security, usability, and flexibility, making it a vital tool in the modern API landscape. Its granular permission control through scopes allows users to grant only the necessary permissions to third-party applications, minimizing the potential impact of security breaches.
Features:
- Delegated authorization framework: Shifts authentication responsibility to the resource server.
- Multiple grant types: Supports diverse application scenarios and security levels.
- Token-based authentication: Uses tokens for secure access to resources.
- Separation of authentication and authorization: Decouples user identity verification from resource access permission.
- Scoped access permissions: Provides granular control over data access.
- Refresh token mechanism: Enables seamless token renewal without user intervention.
Pros:
- Industry standard for API authorization: Wide adoption ensures interoperability and readily available libraries/tools.
- Highly secure when properly implemented: Protects user credentials and minimizes the risk of unauthorized access.
- Supports temporary access without exposing credentials: Access tokens have limited lifespans, reducing the impact of compromised tokens.
- Granular permission control through scopes: Users grant specific permissions, limiting the scope of potential damage.
- Enables third-party integrations without sharing passwords: Enhances security by avoiding the need for direct credential sharing.
- Supports token refreshing without user interaction: Provides seamless continuous access to resources.
Cons:
- Complex to implement correctly: Requires thorough understanding of the protocol and careful implementation.
- Significant overhead for simple APIs: Can be overkill for APIs with minimal security requirements.
- Multiple flows can lead to implementation confusion: Choosing the correct grant type requires careful consideration.
- Requires careful security configuration: Misconfigurations can introduce vulnerabilities.
- Token management adds complexity: Implementing token storage, validation, and refresh mechanisms requires careful planning.
Examples:
- Google's OAuth 2.0 implementation: Used for accessing Google services like Gmail, Drive, and Calendar.
- Microsoft's Azure Active Directory OAuth implementation: Used for accessing Microsoft services and resources.
- Facebook Login API: Allows third-party applications to access user profiles and other Facebook data.
- GitHub's OAuth: Enables access to GitHub repositories and other resources.
- Twitter API authentication: Authorizes applications to interact with the Twitter platform.
Tips:
- Choose the appropriate grant type for your use case: Understand the different grant types and select the one that best fits your application's needs.
- Always validate tokens on your server: Never trust tokens without server-side validation.
- Implement PKCE (Proof Key for Code Exchange) for mobile/SPA applications: Enhances security for applications that cannot store client secrets securely.
- Use short-lived access tokens with refresh tokens: Minimizes the impact of compromised access tokens.
- Validate redirect URIs to prevent token hijacking: Ensure that redirect URIs are registered and validated to prevent malicious actors from intercepting tokens.
- Implement proper state parameter handling to prevent CSRF attacks: Use a random, unpredictable state parameter to protect against Cross-Site Request Forgery attacks.
Popularized By: IETF OAuth Working Group, Google, Facebook, Twitter, Microsoft.
3. JSON Web Tokens (JWT)
JSON Web Token (JWT) is a widely adopted open standard (RFC 7519) for securely transmitting information between parties as a JSON object. Think of it as a digital passport that verifies the identity of a user and grants them access to protected resources. It works by encoding claims (like user ID, email, and permissions) within a compact, self-contained token. This token can be signed using a secret key (symmetric signing) or a public/private key pair (asymmetric signing) to ensure its integrity. Furthermore, JWTs can be encrypted to provide confidentiality, although this is optional. The receiving party can then verify the signature and decrypt the token to retrieve the claims. This stateless approach eliminates the need for constant database lookups, making JWT particularly well-suited for distributed systems and microservices architectures.
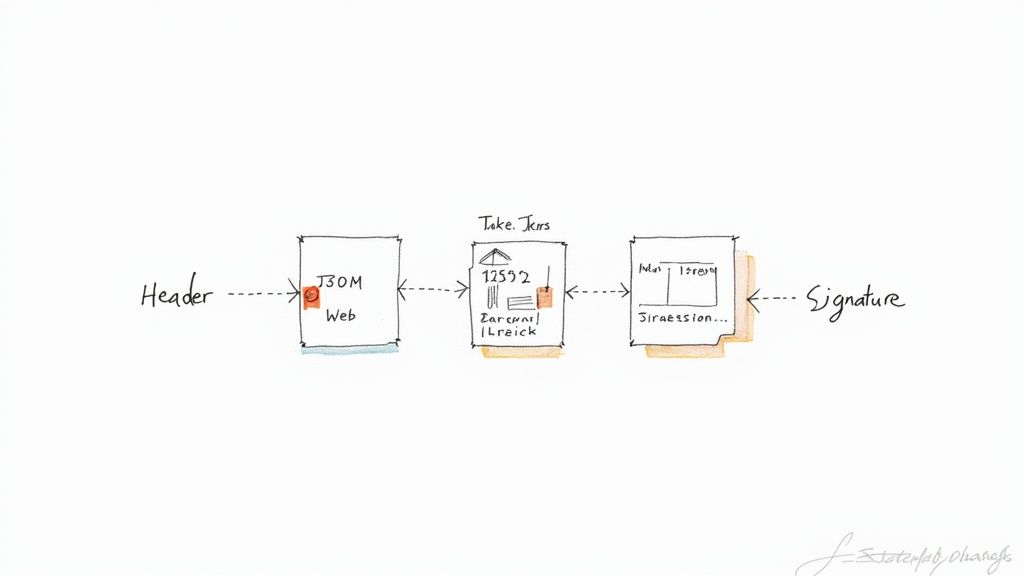
JWTs are structured into three parts: header, payload, and signature. The header describes the token type and hashing algorithm used. The payload contains the claims, which are statements about an entity (typically, the user) and additional metadata. The signature is generated by hashing the header and payload together with a secret key. This structure allows recipients to verify the token's authenticity and ensure that the claims haven't been tampered with.
Features and Benefits:
- Self-contained: All necessary user information is embedded within the token itself.
- Cryptographically Signed: Ensures integrity and prevents tampering.
- Optional Encryption: Provides confidentiality for sensitive data.
- Compact Format: Suitable for HTTP headers and bandwidth-constrained environments.
- Stateless Authentication: Reduces server load and improves performance.
- Standardized Structure: Facilitates interoperability between different systems.
Examples of Successful Implementations:
- Auth0: Uses JWTs extensively for its authentication services.
- Firebase Authentication: Implements JWTs for secure user authentication.
- Okta: Leverages JWTs as a core component of its authentication system.
- AWS Cognito: Employs JWTs for user authentication and authorization.
- Numerous Single Sign-On (SSO) Implementations: JWTs are commonly used to enable seamless access across multiple applications.
Pros:
- Stateless nature reduces database lookups and improves performance.
- Contains all necessary user information (claims), simplifying authorization.
- Can include expiration times and other security controls.
- Works well across different domains and services.
- Relatively simple to implement compared to more complex protocols like OAuth.
- Ideal for microservices architectures.
Cons:
- Tokens cannot be invalidated before expiration, posing a security risk if compromised.
- Token size increases with more claims, potentially impacting performance.
- Security vulnerabilities can arise if implemented incorrectly (e.g., weak signing algorithms).
- Token contents are visible to the client unless encrypted.
- Requires secure key management.
Tips for Implementing JWTs:
- Keep tokens short-lived: Mitigate the risk of compromised tokens.
- Use strong signing algorithms: RS256 (asymmetric) is generally preferred over HS256 (symmetric) for public APIs.
- Include only necessary data in the payload: Minimize token size and improve performance.
- Validate all aspects of the token on each request: Ensure the token's integrity and validity.
- Consider implementing a token blacklist for critical systems: Allows for immediate revocation of compromised tokens.
- Use secure storage mechanisms on the client-side: Protect tokens from theft or unauthorized access.
Why JWT Deserves Its Place in the List:
JWT offers a robust, flexible, and widely adopted solution for API authentication. Its stateless nature, compact format, and ease of implementation make it an excellent choice for modern web applications, particularly those employing microservices architectures. While careful consideration of security best practices is essential, JWT provides a powerful tool for securing APIs and protecting user data. Its popularity and broad adoption within the industry further solidifies its importance for AI professionals, developers, and anyone working with APIs. JWT provides a strong balance between security, performance, and ease of use, making it a top contender for API authentication.
4. Basic Authentication
Basic Authentication is a simple and widely supported authentication method built directly into the HTTP protocol. It's a fundamental approach where the client sends their username and password with every request to the server. This information is included in the Authorization header, formatted as Basic followed by a base64-encoded string of username:password. While straightforward to implement, its simplicity also brings inherent security limitations.
How it Works:
Client Request: The client makes an HTTP request to the server, including the
Authorizationheader. For instance, if the username is "user" and the password is "password", the header would look like this:Authorization: Basic dXNlcjpwYXNzd29yZA==
(where
dXNlcjpwYXNzd29yZA==is the base64 encoding of "user:password")Server Decoding: The server receives the request and decodes the base64-encoded string in the
Authorizationheader to retrieve the username and password.Verification: The server verifies the provided credentials against its user database or authentication system.
Response: If the credentials are valid, the server grants access to the requested resource. If not, it returns a
401 Unauthorizedresponse, prompting the client to provide valid credentials.
Features and Benefits:
- HTTP Standard: Being part of the HTTP standard ensures broad compatibility across clients and servers.
- Simple Implementation: Basic Authentication is remarkably easy to implement on both the client and server sides, requiring minimal code and no external libraries.
- Universal Support: Virtually all HTTP clients and servers natively support Basic Authentication.
- Stateless: The server doesn't need to maintain session information, simplifying implementation and scalability.
Pros:
- Extremely simple to implement and integrate
- Ubiquitous support across platforms and programming languages
- No need for external libraries or dependencies
- Works seamlessly with any standard HTTP client
- No server-side session management required
Cons:
- Security Risk: Credentials are transmitted with every request, making them vulnerable to interception if not used over HTTPS. Base64 encoding is easily reversible and not encryption.
- No Expiration: Credentials remain valid indefinitely until changed, increasing the risk of unauthorized access if compromised.
- Browser Caching: Browsers often cache credentials, making logout procedures less reliable.
- Replay Attacks: Susceptible to replay attacks where captured credentials can be reused.
- Limited Permissions: Basic Authentication doesn't offer granular control over access permissions; users either have full access or no access.
Examples of Successful Implementation (within limitations):
- Legacy Internal APIs: Often used in internal systems where security requirements are less stringent.
- Git over HTTP: Utilized for basic authentication when interacting with Git repositories over HTTP.
- Simple Admin Interfaces: Suitable for basic administrative interfaces with limited functionality.
- Development Environments: Convenient for testing and development purposes where security is not a primary concern.
- Some Legacy CRM and ERP Systems: Still found in some older CRM and ERP systems, although generally being phased out for more secure methods.
Tips for Safe Usage:
- Always Use HTTPS: This is paramount. HTTPS encrypts the communication channel, protecting the credentials during transmission.
- IP Restrictions: Limit access to specific IP addresses or ranges to add an extra layer of security.
- Rate Limiting: Implement rate limiting to mitigate brute-force attacks by restricting the number of login attempts within a given timeframe.
- Strong Password Policies: Enforce strong password policies requiring a combination of uppercase and lowercase letters, numbers, and symbols.
- Consider Alternatives: For production environments and applications handling sensitive data, prioritize more secure authentication methods like OAuth 2.0 or JWT (JSON Web Tokens).
- Combine with Other Security Measures: Use Basic Authentication in conjunction with other security practices like IP whitelisting and multi-factor authentication for enhanced protection.
When and Why to Use Basic Authentication:
Basic Authentication is best suited for scenarios where simplicity and broad compatibility are prioritized over robust security. This typically includes development or testing environments, internal systems with low-security requirements, or legacy applications where other authentication methods are not feasible. However, it is crucial to understand and acknowledge the inherent security limitations and to mitigate the risks as much as possible by following the tips outlined above. For production environments dealing with sensitive data, more secure authentication mechanisms are strongly recommended.
No spam, no nonsense. Pinky promise.
5. OpenID Connect (OIDC)
OpenID Connect (OIDC) is a modern identity layer built on top of the OAuth 2.0 authorization framework. Think of OAuth 2.0 as the foundation for granting access to resources, while OIDC adds the crucial ability to verify who is accessing them. It provides a standardized way for clients to authenticate users and obtain basic profile information, streamlining the login process and enabling single sign-on (SSO).
How it works:
OIDC utilizes a combination of JSON Web Tokens (JWTs), specifically ID tokens, and a dedicated UserInfo endpoint. When a user initiates a login via OIDC, they are redirected to the identity provider (IdP). Upon successful authentication with the IdP, the user is redirected back to the application (client) with an ID token. This ID token contains verified claims about the user, such as their name, email address, and user identifier. The application can then use this ID token to establish the user's identity and grant access to protected resources. Furthermore, the application can use the access token (obtained through OAuth 2.0 flow) to call the UserInfo endpoint and retrieve additional user attributes.
Features and Benefits:
- Identity Layer on top of OAuth 2.0: Leverages the existing OAuth 2.0 framework for authorization, adding a standardized identity layer.
- ID Tokens (JWT): Compact and self-contained tokens containing verifiable user information in a structured format.
- UserInfo Endpoint: Provides a standardized way to fetch additional user profile data.
- Standard Claims: Defines a set of standard claims for consistent user information exchange.
- Discovery Mechanism: Simplifies client configuration through well-known endpoints that provide information about the IdP.
- Multiple Authentication Flows: Supports various flows like authorization code flow with PKCE, implicit flow, and hybrid flow to cater to different application scenarios.
- Single Sign-On (SSO): Enables users to log in once and access multiple applications without re-authenticating.
Examples of Successful Implementation:
- Google Sign-In: One of the most common implementations of OIDC, allowing users to log in to websites and apps using their Google accounts.
- Microsoft Identity Platform (Azure AD): Microsoft's enterprise identity platform uses OIDC for authentication and authorization.
- Okta Identity Cloud & Auth0: Popular identity as a service (IDaaS) platforms that provide OIDC compliant solutions for developers.
- Keycloak: An open-source identity and access management solution that fully supports OIDC.
Pros:
- Combines Authentication and Authorization: Seamless integration of user authentication with resource authorization.
- Standardized Approach: Promotes interoperability and simplifies integration with different IdPs.
- Well-Supported by Major Identity Providers: Wide adoption ensures compatibility and reduces development effort.
- Built-in Mechanism for Obtaining User Information: Simplifies user profile management.
- Strong Security: Provides robust security mechanisms like token signatures and expiration.
Cons:
- More Complex than Simple Token Authentication: Requires a deeper understanding of OAuth 2.0 and JWT.
- Implementation Complexity: Can be challenging to implement correctly on both the client and server side.
- Additional Overhead: Introduces some overhead compared to simpler authentication methods.
- Requires Careful Security Configuration: Misconfiguration can lead to vulnerabilities.
Tips for Implementation:
- Validate ID Tokens: Always validate ID tokens on the client-side to prevent tampering.
- Validate Access Tokens: Verify access tokens on the server-side before granting access to resources.
- Use PKCE: Implement Proof Key for Code Exchange (PKCE) for public clients (like mobile apps and single-page applications) to enhance security.
- Authorization Code Flow + PKCE: Recommended flow for most web applications.
- Verify Token Signatures and Expiration: Ensure the integrity and validity of tokens.
- Use Discovery Documents: Leverage discovery documents to dynamically configure clients based on the IdP's configuration.
- Validate 'nonce' Parameter: Use a 'nonce' parameter to prevent replay attacks.
Why OIDC Deserves Its Place on the List:
In today's interconnected world, secure and streamlined user authentication is critical. OIDC provides a robust and standardized solution for verifying user identities and managing access to resources. Its widespread adoption by major identity providers and support for various authentication flows makes it an essential tool for any developer building modern applications. OIDC offers a balance between security, usability, and interoperability, making it a valuable addition to this list of API authentication methods. Especially for applications needing to integrate with third-party identity providers or requiring SSO capabilities, OIDC is a powerful and versatile solution.
6. HMAC Authentication
HMAC (Hash-based Message Authentication Code) authentication is a robust method for securing APIs by using cryptographic hash functions to verify the authenticity and integrity of requests. It's significantly more secure than simpler methods like API keys or Basic Authentication, making it suitable for sensitive data and critical applications. HMAC earns its spot on this list due to its strong security properties and widespread adoption by major platforms.
How it Works:
HMAC involves a shared secret key between the client and the server. This key is never transmitted over the network. Instead, when a client wants to make a request, it performs the following steps:
- Canonicalization: The request parameters (including a timestamp and often a unique nonce) are organized in a specific, pre-agreed order. This ensures consistency between the client and server calculations.
- Hashing: A cryptographic hash function (like SHA-256 or SHA-512) is applied to the canonicalized request data along with the secret key. This produces a unique HMAC signature.
- Transmission: The client sends the request along with the generated HMAC signature to the server.
- Verification: The server, possessing the same secret key, independently performs the same canonicalization and hashing steps on the received request data. It then compares its calculated signature with the signature received from the client. If the signatures match, the request is authenticated.
Features and Benefits:
- Cryptographic Hash-Based Signatures: Uses secure one-way hash functions to generate signatures, making it computationally infeasible to forge a valid signature without the secret key.
- Request Parameters Included in Signature Calculation: Ensures that the request data hasn't been tampered with in transit.
- Timestamp-Based Protection Against Replay Attacks: The inclusion of a timestamp in the signature calculation prevents attackers from reusing captured requests. The server can reject requests with timestamps outside a specific window (e.g., 5-15 minutes).
- Shared Secret Between Client and Server: Both parties have the same secret key, but it's never transmitted, significantly enhancing security.
- No Transmission of the Actual Secret Key: Eliminates the risk of the key being intercepted during transmission.
Pros:
- More secure than API keys or Basic Auth.
- Prevents request tampering and man-in-the-middle attacks.
- Includes timestamp to prevent replay attacks.
- Secret key never transmitted over the network.
- Works well for server-to-server communication.
Cons:
- Complex implementation compared to simpler methods.
- Requires synchronized clocks between client and server (though a reasonable tolerance is usually acceptable).
- Debugging can be challenging due to signature complexity.
- Risk of timing attacks if implemented incorrectly (though this is less common with modern implementations and libraries).
- Tedious to implement manually in some languages.
Examples of Successful Implementation:
- AWS Signature Version 4 for AWS API authentication
- Azure Storage authentication
- Twilio API authentication
- HubSpot API
- DigitalOcean API
Tips for Implementation:
- Include Timestamp and Nonce: Incorporate a timestamp and a nonce (a random value used only once) in the signature calculation to prevent replay attacks.
- Use a Secure Hash Algorithm: Employ a strong hash algorithm like SHA-256 or SHA-512.
- Ensure Consistent Ordering of Parameters: Maintain the same order of parameters during canonicalization on both the client and server sides.
- Implement Proper Timestamp Validation: Verify that the timestamp in the request is within an acceptable timeframe (e.g., 5-15 minutes of the server's current time) to mitigate replay attacks.
- Consider Using a Library: Leverage existing HMAC libraries for your chosen programming language to simplify implementation and reduce the risk of errors. Manually implementing HMAC can be complex and error-prone.
When and Why to Use HMAC:
HMAC authentication is ideal when security is paramount. Use it when dealing with sensitive data, financial transactions, or any situation where preventing tampering and unauthorized access is critical. It's particularly well-suited for server-to-server communication and applications requiring a high level of trust. While more complex than simpler methods, the added security benefits often outweigh the implementation overhead.
7. Mutual TLS (mTLS)
Mutual TLS (mTLS) is a highly secure authentication method that takes the standard TLS protocol a step further by requiring both the client and the server to present digital certificates for authentication. Think of it like a double-check system. In regular TLS, only the server proves its identity to the client (like showing your ID card). With mTLS, both the client and the server have to present their ID cards, ensuring both parties are who they claim to be. This two-way verification process makes it exceptionally difficult for imposters to intercept or tamper with communications.
This method leverages X.509 digital certificates, issued by a trusted Certificate Authority (CA), to verify identities. The CA acts as a central authority, vouching for the legitimacy of each certificate. When a client connects to a server using mTLS, both present their certificates. Each side then verifies the other's certificate against the trusted CA's chain of trust, confirming its validity and authenticity. This process also checks for certificate revocation, ensuring compromised certificates are no longer accepted. Because this happens at the transport layer, it’s independent of your application code, adding an extra layer of security without requiring significant code changes.
mTLS earns its spot on this list due to its robust security posture, making it ideal for sensitive data and zero-trust environments. It's particularly valuable in scenarios where traditional authentication methods are insufficient. For example, financial institutions rely on mTLS to secure highly sensitive transactions, while healthcare organizations use it to protect patient data exchange. Internal microservices within a zero-trust architecture also benefit greatly from mTLS, ensuring that only authorized services can communicate with each other. Kubernetes uses mTLS to secure its API server, and service meshes like Istio employ it for inter-service communication, further demonstrating its effectiveness in complex, distributed systems. You can learn more about Mutual TLS (mTLS) and explore the benefits of robust security practices for data privacy.
Features and Benefits:
- Two-way Authentication: Both client and server verify each other's identities.
- X.509 Certificates: Industry-standard digital certificates for trusted identity verification.
- Transport Layer Security: Encryption and authentication occur independently of application logic.
- CA-based Trust: Leverages established Certificate Authority trust chains.
- Revocation Mechanisms: Provides ways to invalidate compromised certificates.
Pros:
- Extremely Secure: Offers robust protection against a wide array of attacks.
- Zero-Trust Ready: Perfectly suited for zero-trust security models.
- Ideal for Sensitive Data: Protects high-value transactions and confidential information.
- Microservices Security: Effective for securing communication in distributed systems.
Cons:
- Complex Setup: Requires careful planning and implementation.
- Certificate Management: Ongoing overhead for certificate issuance, renewal, and revocation.
- Debugging Challenges: Troubleshooting connection issues can be more complex.
- Less Suitable for Public APIs: The client-side certificate requirement can be cumbersome for public-facing applications.
Tips for Implementation:
- Lifecycle Management: Implement a robust certificate lifecycle management process.
- Short-Lived Certificates: Use certificates with shorter validity periods to minimize risk.
- Revocation Checking: Configure Certificate Revocation List (CRL) or Online Certificate Status Protocol (OCSP) checking.
- Certificate Management Platform: Consider using a dedicated platform for managing certificates.
- Thorough Testing: Test your mTLS implementation rigorously before deploying to production.
- Defense in Depth: Combine mTLS with application-level authentication for added security.
- Certificate Management Tools: Explore tools like Hashicorp Vault to streamline certificate management.
mTLS is a powerful tool for securing API communications, particularly in environments where security is paramount. By understanding its strengths and weaknesses, and following best practices for implementation, you can leverage mTLS to significantly enhance the security posture of your applications and services.
7-Point API Authentication Comparison
| Authentication Method | Implementation Complexity (🔄) | Resource Requirements (⚡) | Expected Outcomes (📊) | Ideal Use Cases | Key Advantages (⭐) | Tips (💡) |
|---|---|---|---|---|---|---|
| API Keys | Low; straightforward integration | Minimal; stateless token usage | Fast responses with basic identification | Public/internal APIs with low sensitivity | Easy to implement, low latency | Use HTTPS, implement rate limiting, and rotate keys regularly |
| OAuth 2.0 | High; involves multiple flows | Moderate to high; token management overhead | Robust, flexible delegated authorization | Third-party integrations, accessing user data | Granular permission control, industry-standard | Validate tokens, select appropriate grant types, and use PKCE |
| JSON Web Tokens (JWT) | Moderate; simpler than OAuth 2.0 | Low; leverages stateless authentication | Efficient self-contained user verification | Microservices, SSO, and distributed systems | Reduces database lookups with embedded claims | Use strong signing algorithms & short token lifespan |
| Basic Authentication | Very low; extremely simple setup | Minimal; native HTTP support | Quick authentication with basic security | Legacy systems, internal tools, simple admin access | Universal compatibility and ease of implementation | Always use HTTPS and consider IP restrictions |
| OpenID Connect (OIDC) | High; builds on OAuth 2.0 with identity layer | High; due to token validation and discovery mechanisms | Strong identity verification and SSO capabilities | Federated identity and consumer-facing web apps | Combines authentication with authorization mechanisms | Validate ID tokens thoroughly; use recommended flows & PKCE |
| HMAC Authentication | High; involves cryptographic signature calculation | Moderate; requires hash computations and time sync | Secure, tamper-proof communication with message integrity | Server-to-server communications, sensitive data exchange | Enhanced security with cryptographic verification | Use secure hash algorithms and ensure synchronized clocks |
| Mutual TLS (mTLS) | Very high; complex certificate management | High; requires generating and validating certificates | Highest security with mutual identity verification | Critical APIs, zero-trust environments, highly sensitive data | Robust two-way authentication with strong encryption | Implement proper certificate lifecycle management and revocation |
Securing the Future of Your APIs
In today's interconnected world, API security is paramount. We've explored seven key authentication methods: API Keys, OAuth 2.0, JSON Web Tokens (JWT), Basic Authentication, OpenID Connect (OIDC), HMAC Authentication, and Mutual TLS (mTLS). Each offers a different level of security and complexity, catering to diverse needs and architectures. From simple key-based access to robust mutual authentication, understanding these methods is essential for any developer, entrepreneur, or AI professional working with APIs.
The key takeaway is that there's no one-size-fits-all solution. While API keys are easy to implement, they might not be suitable for highly sensitive data. Methods like OAuth 2.0 and mTLS provide stronger security but require more careful planning and implementation. Choosing the right method depends on balancing security requirements with the complexity of your system and the sensitivity of the data being exchanged.
So, what are your next steps? Start by evaluating your current API integrations. Identify potential vulnerabilities and consider which authentication methods best suit your specific needs. Research each method in detail and experiment with different implementations. Testing your APIs thoroughly before deployment is crucial for ensuring their reliability and security. For a deeper dive into API testing and its importance, check out this resource on API testing. Remember, security is an ongoing process, not a one-time fix.
Mastering these API authentication methods is not just a technical skill; it's an investment in the future of your projects. By prioritizing security, you protect your data, build trust with your users, and ensure the long-term success of your applications and integrations. As AI and interconnected systems continue to evolve, robust API security will be more critical than ever. Embrace these practices, and you'll be well-equipped to navigate the ever-changing digital landscape.